Strategy ONE
Windows Secure Deployment
A secure deployment is strongly recommended. In a secure deployment scenario, you add HTTPS/TLS support to the Library application. The server processes will remain on the same machine, but will communicate with each other through a secure channel.
The following diagram shows the secure deployment:
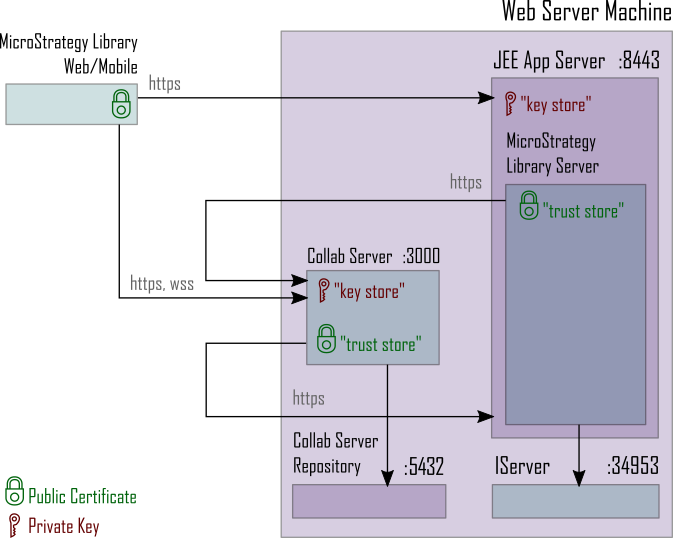
Perform the following procedure to enable secure communication between the Library applications and services on a Windows server. These instructions assume that a default deployment has already been completed, and Intelligence server has already been TLS enabled.
Prepare Files for Secure Deployment
Contact your system administrator to obtain the following files and information:
- A “key store” file in PKCS12 or PFX format which contains the private key and the public certificate for this machine. In the example this file is saved as
keystore.pfxUse this same file for both Collaboration server and Tomcat.
The Collaboration server only supports PKCS12 or PFX format.
- The passphrase used to create the key store file.
The passphrase is needed to read the contents of the key store. In the example, the passphrase is "keystore_password".
- If the server certificate is not signed by a public certificate authority, then collect the Root CA certificate in the chain. The 'certificate' file allows Collaboration server to open a secure connection to the Library server.
- A “trust store” file (that can be created from the certificates) and the passphrase used.
The trust store file is used by the Library server to open a secure connection to the Collaboration server.
This is only required if the certificate is not signed by a public certificate authority.
In the example, the file is saved as
truststore.pfxand the passphrase is "truststore_password".
Copy the files obtained in step 1 into the following directory:
C:\Program Files (x86)\MicroStrategy\Collaboration Server
Set Up Secure JEE App Server
Configure Tomcat to use HTTPS to configure Tomcat to be a secure endpoint:
-
Open the following directory:
<TOMCAT_INSTALL_DIRECTORY>\conf - Open the
server.xmlfile with a text editor. -
Look for the Connector element whose port is 8443. Ensure it is not commented out. If Connector doesn't exist, add it.
-
Edit the 'keystoreFile' and 'keystorePass' attributes of this element.
Copy<Connector
protocol="org.apache.coyote.http11.Http11NioProtocol"
port="8443"
maxThreads="200"
scheme="https"
secure="true"
SSLEnabled="true">
<SSLHostConfig certificateVerification="none" sslProtocol="TLS">
<Certificate certificateKeystorePassword="<keystore_passphrase>" certificateKeystoreFile="C:\Program Files (x86)\MicroStrategy\Collaboration Server\keystore.pfx"/>
</SSLHostConfig>
</Connector> -
Save and close the file.
You can refer to more detailed instruction from Tomcat documentation.
Set Up Secure Strategy Library Server
Modify the Strategy Library server settings to open a secure connection to the Collaboration server:
-
Navigate to the following directory:
<TOMCAT_INSTALL_DIRECTORY>\webapps\MicroStrategyLibrary\WEB-INF\classes\config -
Edit
configOverride.propertiesfile:Copyservices.collaboration.baseURL=https://<FQDN>:3000
// set tlsEnabled to true only when the certificate is not assigned by a public certificate authority
services.collaboration.tlsEnabled=true
trustStore.path=\WEB-INF\truststore.pfx
trustStore.passphrase=<truststore_password>All parameters are case sensitive. Read the instructions in Strategy Library Server Configuration Properties for more information.
-
Save and close the file.
-
Restart Tomcat Server.
-
Verify that the Strategy Library server is running:
- Open a web browser and enter https://FQDN:8443/MicroStrategyLibrary
-
If you see login page, then Strategy Library server is working.
Set Up Secure Collaboration Server
Modify the Collaboration server settings:
-
Edit the
config.jsonfile located in:C:\Program Files (x86)\MicroStrategy\Collaboration Server -
Insert the following lines into the file. These reference the security artifacts we created earlier.
Copy"enableTls": true,
"keystoreFile": "C:/Program Files (x86)/MicroStrategy/Collaboration Server/keystore.pfx",
"passphrase": "<keystore_passphrase>",
"trustedCerts": [ "C:/Program Files (x86)/MicroStrategy/Collaboration Server/certificate.pem" ]All parameters are case sensitive. Read the instructions inCollaboration Server Configuration Properties for more information.
-
Modify the
authorizationServerUrlfield in theconfig.jsonfile to specify “https” , the HTTPS port (8443) and replace “localhost” with the fully qualified domain name (FQDN) for this machine.It should look like the following:
authorizationServerUrl: https://<FQDN>:8443/MicroStrategyLibrary/api -
Make sure the file is still valid JSON. Copy the text into an Internet JSON validator to verify.
-
Save the file.
-
Restart the Collaboration server.
-
Verify that the Collaboration server is running:
-
Open a web browser and enter
https://FQDN:3000/status -
If you see a web page (with no errors), then Collaboration server is working.
-
Note the following:
-
JEE App Server – key store
This is used to establish the identity of the JEE App Server, which houses the Strategy Library server. This is changed in a system configuration file. For example, the
server.xmlfile in a Tomcat installation. -
Strategy Library server – trust store
Used to verify identity of the Collaboration server and/or Intelligence server for outgoing HTTPS/TLS calls when the Server certificate is not signed by a public certificate authority. The trust store is configured in the
configOverride.propertiesfile. -
Strategy Collaboration server – key store / certificate
The key store is used for trusted communication between the Library Web/Mobile Client and the Collaboration server. The certificate is used to verify the identity of the Library server. The key store and certificates are configured in the
config.jsonfile.
