Strategy One
Enable Single Sign-On with OIDC Authentication
Starting in Strategy One (January 2026), you can automatically set a user’s language by passing a locale value through a OIDC claim during authentication. Library extracts the language from the OIDC claim and sets it to the user at login.
Starting in Strategy One (December 2025), you can add an LDAP authentication distinguished name to your OIDC authentication to locate user and group objects.
Starting in MicroStrategy ONE (December 2024), you can add system prompt mapping and nested groups to your OIDC authentication. This additional customization provides more granular control over user access and improves the overall security and usability of your system.
You can enable single sign-on with OpenID Connection (OIDC) authentication for Azure, Okta, and more.
The ability to view or edit certain settings is determined by a user's privileges. All necessary privileges are included in the Administrator role by default. You must belong to the System Administrators group to use this feature.
See Enable Single Sign-On with OIDC Authentication in the System Administration Help for more details.
- Open the Workstation window.
-
In the Navigation pane, click Environments.
- Right-click an environment and choose Configure Enterprise Security > OIDC.
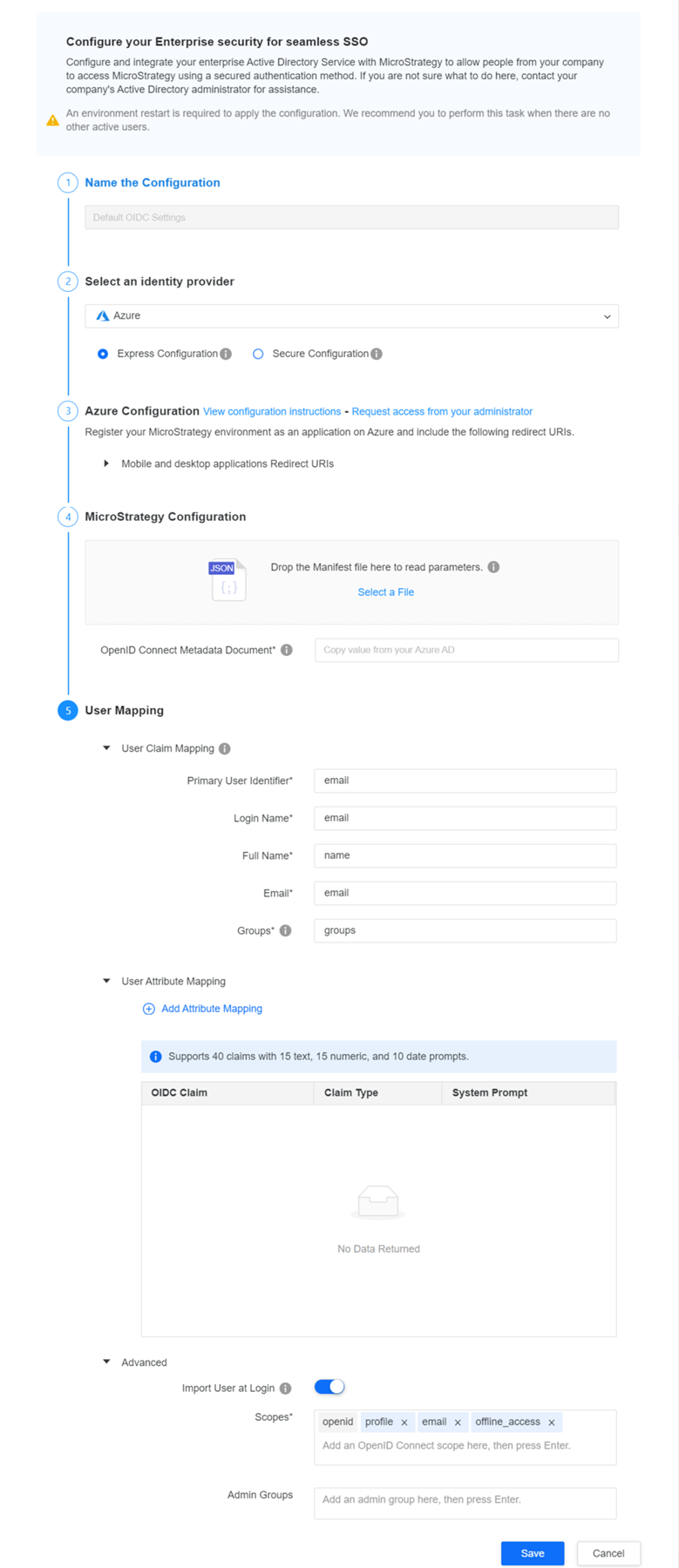
- In Step 1: Name the Configuration, type a name.
- In Step 2: Select an identity provider, select an identity provider.
- In Step 3: Identity Provider Configuration, click View configuration instruction to view a step-by-step configuration guide. Use the instructions to complete steps 3 and 4. Starting in MicroStrategy 2021 Update 10, if your IdP supports single logout, you can enable it using Enable Single Logout with OIDC Authentication.
- If you need assistance from your administrator that is in charge of enterprise Identity and Access Management (IAM), click Request access from your administrator.
-
In Step 5: User Mapping, configure the following settings for IAM user mapping...
User Claim Mapping Expand to enter OIDC claims to identify users and display their info.
MicroStrategy ONE (December 2024) adds support for nested groups in OIDC authentication. Enter
\between each nested group. For example, if you have a group "B" that is nested under group "A", enterA\Bin Groups.User Attribute Mapping Expand to enter prompts to map attributes for system prompts.
Starting in MicroStrategy ONE (December 2024), use SSO system prompts as everyday system prompts to create a report filter or security filter. For more information on Intelligence Server system prompts, see KB10937.
There are 40 SSO system prompts that you can use, 15 with text type, 15 with numeric type, and 10 with date type. For data type formats, the following formats are supported:
-
Raw timestamp. For example, 1674304586.
-
String with time. For example, 2023-01-21 20:36:26.
-
String without time. For example, 2024-08-07.
Primary User Identifier Enter the OIDC claim used to identify users. By default, the OIDC claim is email.
Login Name: Enter the OIDC claim for the login name. By default, the OIDC claim is name.
Full name Enter the OIDC claim used for display users’ full names in Strategy. By default, the OIDC claim attribute is name.
Distinguished Name: Starting in Strategy One (December 2025), enter the OIDC claim for the LDAP distinguished name. This claim mapping is optional.
Email Enter the OIDC claim used as the user's email in Strategy. By default, the OIDC claim attribute is email.
Language Enter the name of the OIDC claim that contains the user's language. An available language attribute is automatically assigned to the mapping.
Groups: Starting in Strategy One (December 2025), enter the OIDC claim for the user group. By default, the OIDC claim attribute is groups. For nested group structures, use backslahes to represent the hierarchy. For example, if you have a group "B" nested under group "A", enter "A\B" in the input box.
Group Format: Starting in Strategy One (December 2025), decide how the Groups claim is parsed. There are 2 options:
-
Simple: Use the Groups claim values as the user group name. This is the default option.
-
Distinguished Name: Parse each Groups claim value as an LDAP distinguished name and extract the common name (CN) as the user group name.
Advanced Expand to enter advanced user mapping settings.
Import User at Login Activate this toggle to allow users from your active directory to use their credentials to log in to Strategy.
-
-
If Okta is selected as the identity provider, in Step 6: Test Configuration, click Test Configuration to test with the credentials you provided above.
-
Click Save.
- Access the Library Admin page to complete additional steps before the OIDC authentication takes effect.