Strategy One
Configure the Library Server as SCIM 2.0 Service Provider
Starting in Strategy One (February 2026), you can synchronize system prompts using SCIM 2.0 protocol, providing capability for third party identity providers to predefine users' system prompts.
Starting in Strategy One (January 2026), you can synchronize user language settings using System for Cross-Domain Identity Management (SCIM) 2.0 protocol.
Strategy One (September 2025) adds support for System for Cross-Domain Identity Management (SCIM) 2.0 protocol. This protocol allows third party identity providers to automatically provision and manage users and groups on the Library server using a list of standard REST API requests. This addition includes the following functionality:
-
Support for user and group import and sync
-
Certified with identity providers like Okta and Azure
-
Support for bearer authentication
Prerequisites
-
Your identity provider supports SCIM 2.0 provisioning with bearer authentication.
-
Your Library server is hosted in a network that your identity provider can send network requests to.
-
Your administrator account must have the following Server - Intelligence privileges:
-
Bypass all object security access checks
-
Create and edit users and groups
-
Configure security settings
-
Enable user
-
Administer environment
-
Use Workstation
-
Enable and Configure SCIM 2.0 Service on Workstation
-
Open the Workstation Window and connect to your environment.
-
Right-click your environment and choose Configure Enterprise Security and Configure SCIM.
-
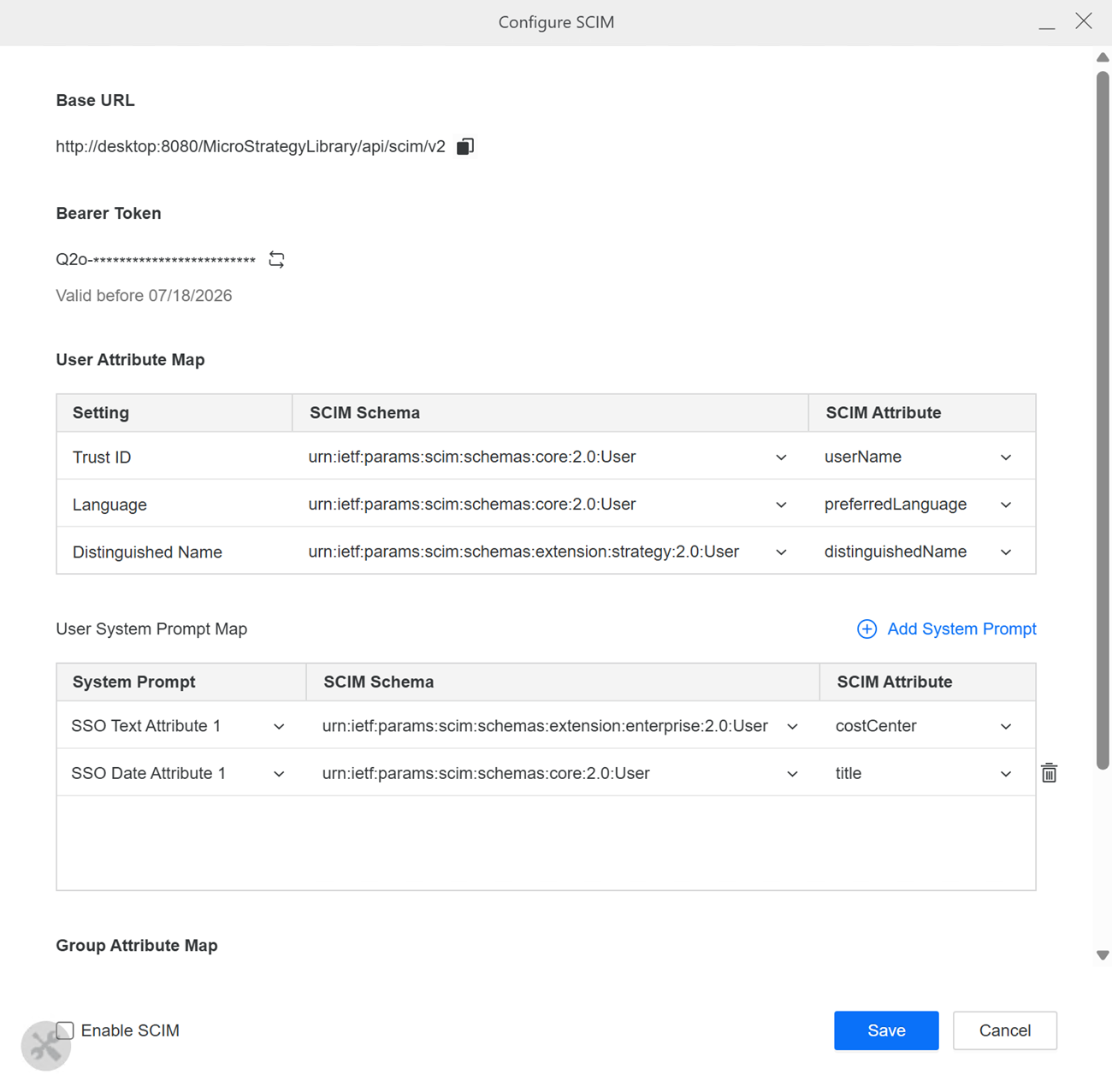
In Bearer Token, choose a token expiration time from the drop-down list and click Generate.
-
Click Copy next to the Base URL and Bearer Token. Use these values to configure provisioning your identity provider.
-
Customize attribute mapping for users or groups created using SCIM:
User Attribute Map
-
Trust ID. This field is required.
-
Schema:
urn:ietf:params:scim:schemas:core:2.0:User -
Attribute:
userName
-
-
Language. This field is optional.
-
Schema:
urn:ietf:params:scim:schemas:core:2.0:User -
Attribute:
preferredLanguageorlocale -
Distinguished Name. This field is optional.
-
Schema:
urn:itef:params:scim:schemas:extension:strategy:2.0:User -
Attribute:
distinguishedName
-
User System Prompt Map
Starting in Strategy One (February 2026), to predefine users' system prompts, click Add System Prompt and choose the following values:
-
System Prompt. Choose a text, numeric, or date attribute system prompt.
-
SCIM Schema. Choose from the following:
-
urn:ietf:params:scim:schemas:core:2.0:User -
urn:ietf:params:scim:schemas:extension:strategy:2.0:User -
urn:ietf:params:scim:schemas:extension:enterprise:2.0:User
-
-
SCIM Attribute. Choose an attribute type.
Group Attribute Map
-
Distinguished Name. This field is optional.
-
Schema:
urn:ietf:params:scim:schemas:extension:strategy:2.0:Group -
Attribute:
distinguishedName
-
Most SCIM user/group attributes have fixed mappings to Intelligence Server user/group attributes. You can customize the mapping in the identity provider configuration. For an attribute mapping list, see SCIM 2.0 Attribute Mapping.
-
-
If you do not have a trusted relationship between the Web Server and Intelligence Server, click Create Trusted Relationship.
You must restart the Library server after creating or deleting a trust relationship.
-
Select the check box next to Enable SCIM and click Save.
Configure SCIM 2.0 Provisioning on Identity Providers
Identity provider configurations vary by vendor but all providers require the following information from Workstation:
-
SCIM Base URL: The base URL for SCIM API calls.
-
SCIM Bearer Token: The token for SCIM API authentication.
Identity providers often allow you to map user and group attributes from their system to SCIM attributes. When you map user and group attributes, the user information is imported into the Intelligence server.
System prompt attribute configuration is similar to other attributes. Ensure the attributes configured in the user system prompt map are mapped in the identity provider.
For example, see the following topics on integrating the Strategy Library SCIM API into different identity providers:
SCIM 2.0 Attribute Mapping
See the following predefined user and group attribute mappings between the Intelligence Server and SCIM 2.0.
Supported Schemas
Strategy supports reading attributes from three standard and two custom user/group schemas:
|
Schema Type |
Schema |
Description |
|---|---|---|
|
User |
urn:ietf:params:scim:schemas:core:2.0:User |
SCIM 2.0 core user schema |
|
urn:ietf:params:scim:schemas:extension:enterprise:2.0:User |
SCIM 2.0 enterprise user schema |
|
|
urn:ietf:params:scim:schemas:extension:strategy:2.0:User |
Custom user schema from Strategy Library |
|
|
Group |
urn:ietf:params:scim:schemas:core:2.0:Group |
SCIM 2.0 core group schema |
|
urn:ietf:params:scim:schemas:extension:strategy:2.0:Group |
Custom group schema from Strategy Library |
Supported User Attributes
The Library server maps user information from the following SCIM attributes during import and sync:
|
Library User Attribute |
Target SCIM Attribute Schema |
Target SCIM Attribute |
|---|---|---|
|
Object ID |
urn:ietf:params:scim:schemas:core:2.0:User |
id |
|
Time created |
urn:ietf:params:scim:schemas:core:2.0:User |
meta.created |
| Time modified |
urn:ietf:params:scim:schemas:core:2.0:User |
meta.lastModified |
| Username (login) |
urn:ietf:params:scim:schemas:core:2.0:User |
userName |
|
Full name |
urn:ietf:params:scim:schemas:core:2.0:User |
displayName |
| Enabled user |
urn:ietf:params:scim:schemas:core:2.0:User |
active |
| Email address |
urn:ietf:params:scim:schemas:core:2.0:User |
emails[primary eq true].value or emails[0].value id, if primary email is not found |
The Library server also allows custom mapping for the following user attributes:
|
Library User Attribute |
Target SCIM Attribute Schema |
Target SCIM Attribute |
|---|---|---|
|
Trusted authenticated request user ID |
urn:ietf:params:scim:schemas:core:2.0:User |
userName |
|
LDAP distinguished name (DN) |
urn:ietf:params:scim:schemas:extension:2.0:User |
distinguishedName |
Trusted authenticated request user ID is a required Intelligence Server attribute. Always pass the corresponding SCIM attribute during user sync.
Supported Group Attributes
The Library server maps group information from the following SCIM attributes during group import and sync:
|
Library Group Attribute |
Target SCIM Attribute Schema |
Target SCIM Attribute |
|---|---|---|
|
object ID |
urn:ietf:params:scim:schemas:core:2.0:Group |
id |
|
time created |
urn:ietf:params:scim:schemas:core:2.0:Group |
meta.created |
| time modified |
urn:ietf:params:scim:schemas:core:2.0:Group |
meta.lastModified |
|
user group name |
urn:ietf:params:scim:schemas:core:2.0:Group |
displayName |
The Library server allows custom mapping for several group attributes:
|
Library Group Attribute |
Default Target SCIM Attribute Schema |
Default Target SCIM Attribute |
|---|---|---|
|
LDAP distinguished name (DN) |
urn:ietf:params:scim:schemas:extension:strategy:2.0:Group |
distinguishedName |
Known Limitations on SCIM API
Intelligence Server Users/Groups Limitations
The Intelligence Server third party user/group attribute requirements include the following:
-
Full names cannot contain special characters such as \, ", [], or .
-
Trust IDs must be unique and cannot be null or empty.
-
User emails cannot be null or empty.
-
The SCIM API stores one email per user.
-
Attribute mapping customization does not support mapping sub-attributes of complex attribute types (for example,
name.familyName)
SCIM Endpoint Limitations
GET Users
-
Only users with a trust ID are returned.
-
Sorting parameters (for example,
sortByorsortOrder) are not supported. -
For paging (count), the default value is
1000and the maximum value is10000. -
The filter parameter only supports
userName eq <value>. -
The
totalResultsvalue in the response is not an accurate number. It indicates if more users exist.
GET Groups
-
Sorting parameters (for example,
sortByorsortOrder) are not supported. -
For paging (count), the default value is
1000and the maximum value is10000. -
The filter parameter only supports
displayName eq <value>. -
The
totalResultsvalue in the response is not an accurate number. It indicates if more users exist. -
Members are only returned by default if the
displayNamefilter or members in the attributes parameter is defined.
PATCH Users/Groups
Complex value/path filters are not supported. If you use these filters, you will receive a 400 status code and an invalidValue error.
Limitations of supported languages
Strategy Library only supports the locale tags below for synchronizing language, unsupported tags will be ignored.
|
Locale Tags |
Language Name |
|---|---|
|
da-DK |
Danish (Denmark) |
|
de-CH |
German (Switzerland) |
|
de-DE |
German (Germany) |
|
en-GB |
English (United Kingdom) |
|
en-US |
English (United States) |
|
es-ES |
Spanish (Spain) |
|
fr-CH |
French (Switzerland) |
|
fr-FR |
French (France) |
|
it-CH |
Italian (Switzerland) |
|
it-IT |
Italian (Italy) |
|
ja-JP |
Japanese |
|
ko-KR |
Korean |
|
nl-NL |
Dutch (Netherlands) |
|
pl-PL |
Polish |
|
pt-BR |
Portuguese (Brazil) |
|
ru-RU |
Russian |
|
sv-SE |
Swedish (Sweden) |
|
zh-CN |
Chinese (Simplified) |
|
zh-TW |
Chinese (Traditional) |
The language tags below are supported and can be converted to locale tags automatically. Country tags such as US/CN are not supported.
|
Language Tags |
Converted Locale Tags |
|---|---|
|
da |
da-DK |
|
de |
de-DE |
|
en |
en-US |
|
es |
es-ES |
|
fr |
fr-FR |
|
it |
it-IT |
|
ja |
ja-JP |
|
ko |
ko-KR |
|
nl |
nl-NL |
|
pl |
pl-PL |
|
ru |
ru-RU |
|
sv |
sv-SE |
|
zh |
zh-CN |
Language Troubleshooting Tips
I changed the preferredLanguage to zh-CN in the IDP, but the user’s language is not updated.
This is most likely because the user’s language has been set before. The user’s language can be synchronized via SCIM only if it is not set before. Check the user’s language in the User Editor under Internationalization options.
I mapped the locale SCIM attribute to the language, and used LDAP as IDP’s source, but the user’s language cannot be updated.
LDAP uses country code as the locale, which is not supported by Strategy Library. Use preferredLanguage if LDAP is used as IDP’s source.
I created a user in IDP but didn’t set the user’s language at the first time. After I set it later, the language is not synchronized.
This is most likely because the IDP sets default language for users and the user has been synchronized to Strategy Library. To support user-specific language preferences, avoid setting a default language at the IDP level.
User Deletion Behavior by a SCIM Endpoint
When a user is deleted by a SCIM endpoint:
-
The Intelligence Server does not delete all profiles.
-
The Intelligence Server does not delete the user's content in the profile, but the file owner is updated to Administrator.
-
If a subscription only has the deleted user as a recipient, the subscription is also deleted.
-
If a subscription has the deleted user and other users as recipients, the deleted user is removed from the recipients list.
Synchronize System Prompts Limitations
Limitations Clearing System Prompts for PingFederate
Strategy APIs support clearing system prompts, but PingFederate does not.
If you clear the fields that map to system prompts, PingFederate will retrieve the current system prompts from Strategy and update the system prompts with the origin system prompts for cleared fields.
Limitations of Supported Date Type System Prompts
The Strategy Library only supports the following date formats. Invalid inputs will be ignored.
-
Epoch seconds
-
YYYY-MM-DD
-
YYYY-MM-DDTHH:MM:SS
-
ISO instant formatter
