Strategy One
Enabling OIDC Authentication for JSP Web and Mobile
You can configure Strategy Web and Strategy Mobile to work with OIDC compliant Identity providers. To complete the set up in this document, a basic understanding of OIDC workflows is required.
Although the following prerequisites and procedures refer to Strategy Web, the same information applies to Strategy Mobile, except where noted.
Before you begin configuring Strategy Web to support single sign-on, make sure you have done the following:
- Deployed an OIDC application in identity provider (IdP) infrastructure. Take note of the client ID, client secret key (not required for the PKCE method), and issuer details for future reference.
- Verified that Strategy Web is running on a JSP server.
- Deployed Strategy Web on this web application server. Deploy the Strategy Web WAR file on the web application server in accordance with your web application server documentation.
Configuring OIDC authentication for Strategy Web
To configure OIDC authentication, you must setup a trusted relationship between the Web and Intelligence servers. This is done on the Administrator Page. Open the admin page for your web application. Then, connect to the Intelligence Server you want to use.
Establish trust between the server and Intelligence Server:
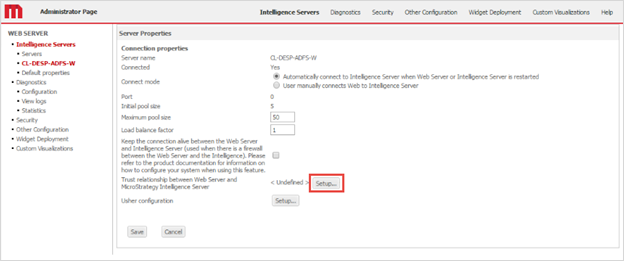
- Open the Server properties editor.
-
Next to Trust relationship between Strategy Web Server and Strategy Intelligence Server, click Setup.
- Enter the Intelligence Server administrator credentials.
- Click Create Trust relationship.
Enable OIDC Authentication
- In Strategy Web Admin, go to the Default Properties screen.
- Enable the OIDC authentication checkbox..
-
In OIDC Configuration, provide the Client ID, Client Secret, Issuer and Native Client ID.
The client ID and native client ID are the same for Strategy Web.
-
Under Claim Map, provide the scope to map IDP users with Strategy users.
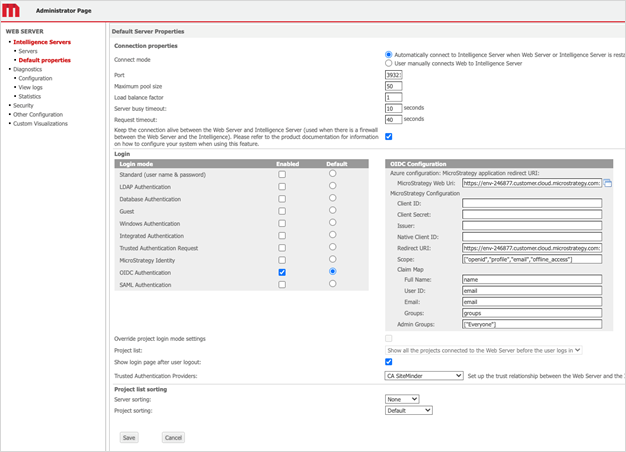
Full Name: User display name attribute
User ID: User distinguished login attribute
Email Attribute: User email address attribute
Group Attribute: User group attribute
Admin Groups: Defines groups that can access the Administrator page. Use commas to define multiple groups. There should be no spaces in front of or behind commas. To allow IdPGroupA and IdPGroupB users to access the Administrator page, the configuration is: Admin Groups: [“IdPGroupA,IdPGroupB”].
For more information on mapping users between a OIDC IdP and Strategy, see Mapping OIDC Users to MicroStrategy.
- Click Save and restart the Web server.
Web Admin Page Authentication
In MicroStrategy 2021 Update 2 or later, the Web admin pages support OIDC and basic authentication when OIDC authentication is enabled. The admin pages authentication is governed by the springAdminAuthMethod parameter located in the WEB-INF/xml/sys_defaults.properties file.
There are two possible values for the springAdminAuthMethod parameter:
-
springAdminAuthMethod = 1(Default)The default value of the
springAdminAuthMethodparameter is 1. This means the Web admin pages are protected by basic authentication. -
springAdminAuthMethod = 2When the
springAdminAuthMethodis set to 2, the Web admin pages are protected by the OIDC admin groups mentioned in the OIDC configuration form. These admin groups are linked to the groups on the Identity Provider(IDP) side. The members who belong to the IDP admin groups can only access the admin pages. Users that do not belong to the admin group receive a 403 Forbidden error.
The administrator can change the parameter value per the requirements. A web application server restart is required for the changes to take effect.
Configure OIDC Logging
-
Locate the
log4j2.propertiesfile in theWEB-INF/classesfolder. -
Modify the
property.filenameproperty to point to the folder where you want the OIDC logs stored.It is not recommended to leave the file as is, since the relative file path is very unreliable and can end up anywhere. The file usually cannot be found in the Web application folder. Use full file paths here to fully control the log location.
In a Windows environment, the file path must be in Java format. This means you either need to change each backslash ("\") to a slash ("/") or escape the backslash with another one ("\\"). You can also shorten the path by referring to the Tomcat base folder as a variable, as shown below.
Copy${catalina.home}/webapps/MicroStrategy/WEB-INF/log/OIDC/OIDC.logFor troubleshooting purposes it is recommended to first change the level of
org.springframework, that is thelogger.c.levelproperty, todebugand leave everything else as the default. This generates a clean log with all OIDC messages, along with any errors or exceptions. -
Restart the Web application server to apply all changes.
If you have a problem accessing the Strategy Web Administrator page, close and reopen your web browser to clear the old browser cache.
