Strategy ONE
Enable Multiple OIDC and SAML Configurations
Starting in MicroStrategy ONE (September 2024), MicroStrategy supports multiple OIDC and SAML configurations. This allows different applications to utilize SAML with various identity providers (IDPs) or OIDC with different identity access management systems (IAMs).
Configure Multiple OIDC/SAML Configurations on the Library Server
-
Open Workstation.
-
In the Navigation pane, click Enterprise Security.
-
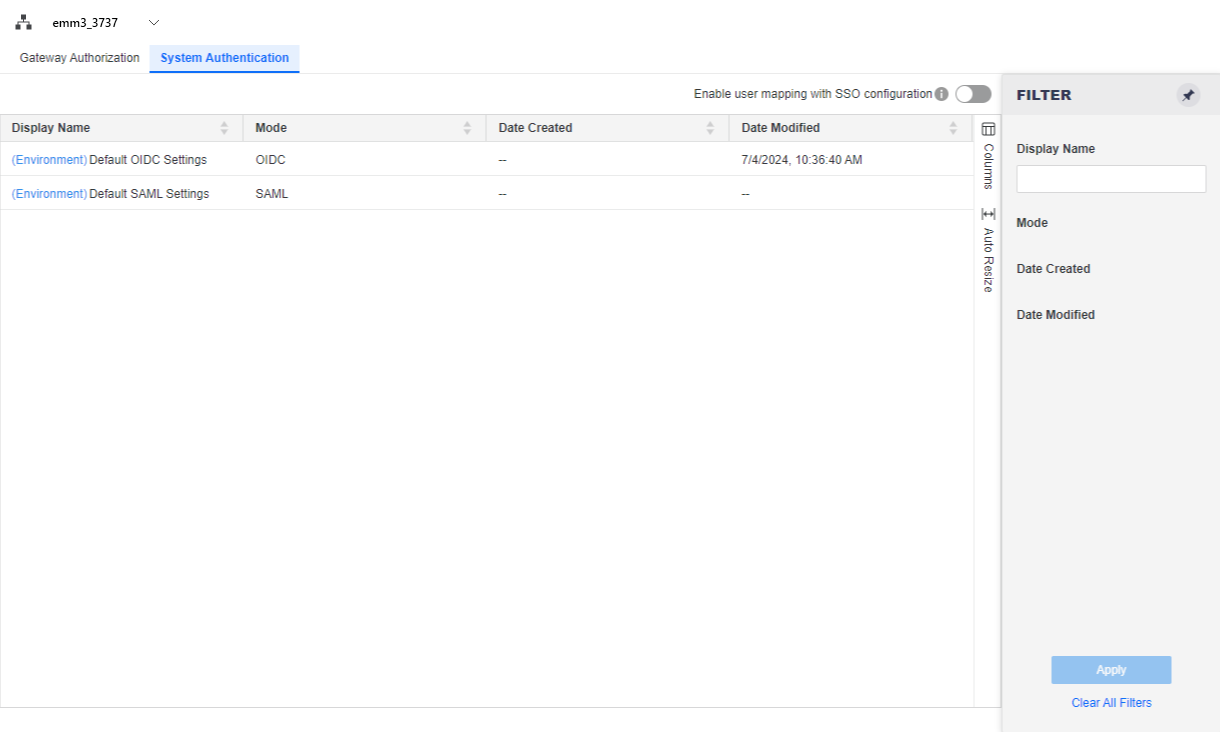
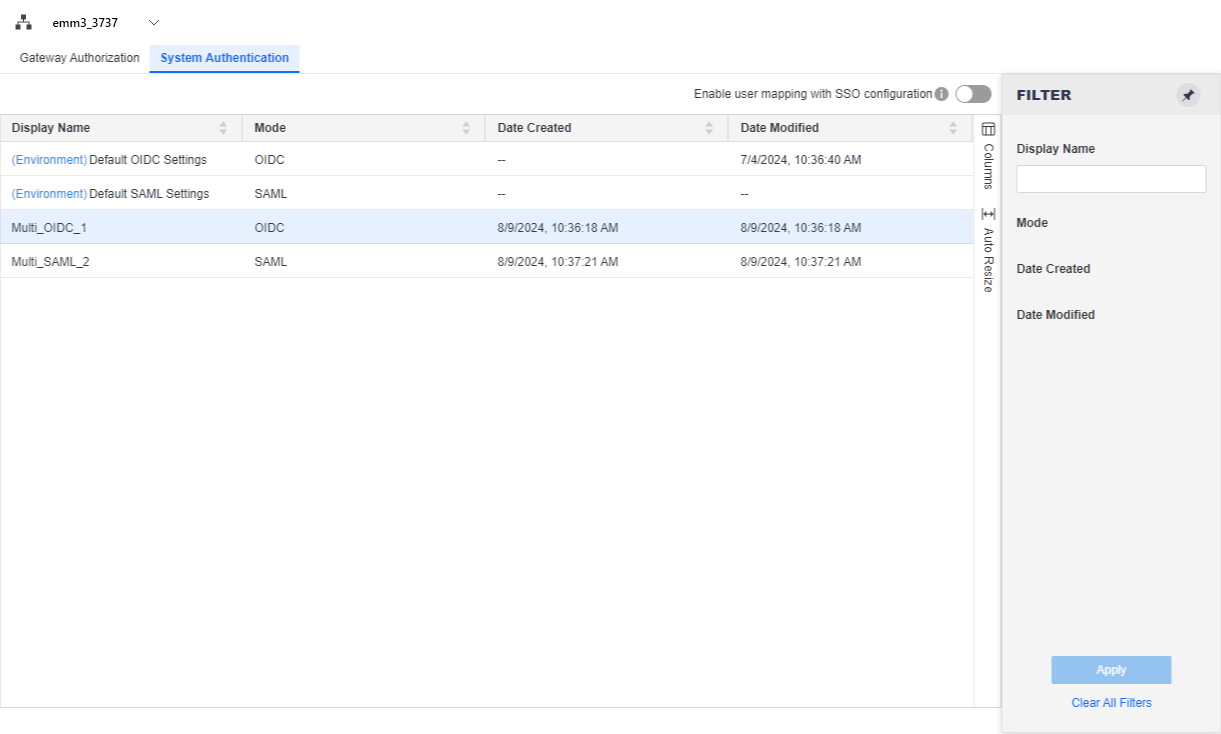
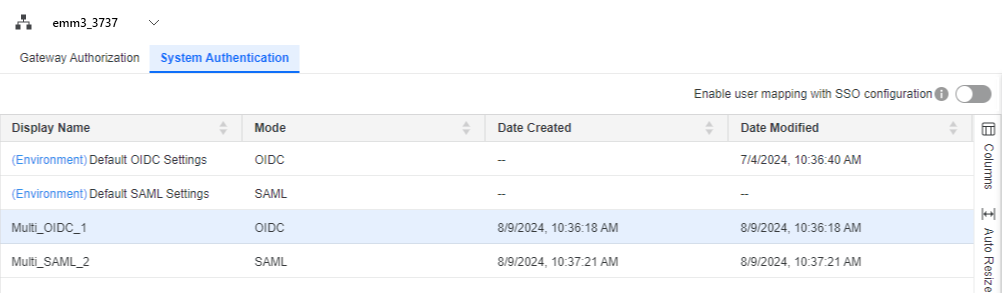
Click System Authentication to display your OIDC/SAML configurations. By default, there are server-level configurations for OIDC and SAML.
-
In the Navigation pane, click
 , next to Enterprise Security.
, next to Enterprise Security. -
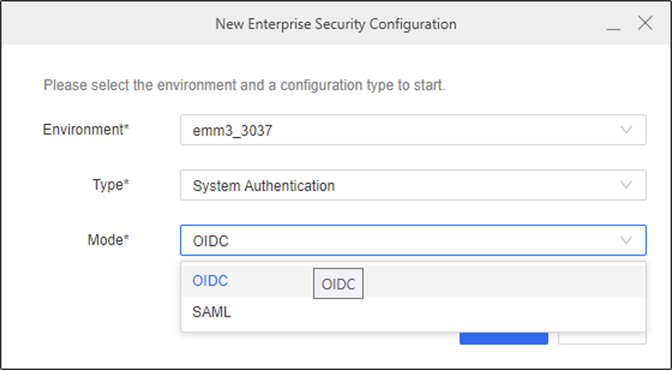
In Type, select System Authentication and in Mode, select OIDC or SAML.
-
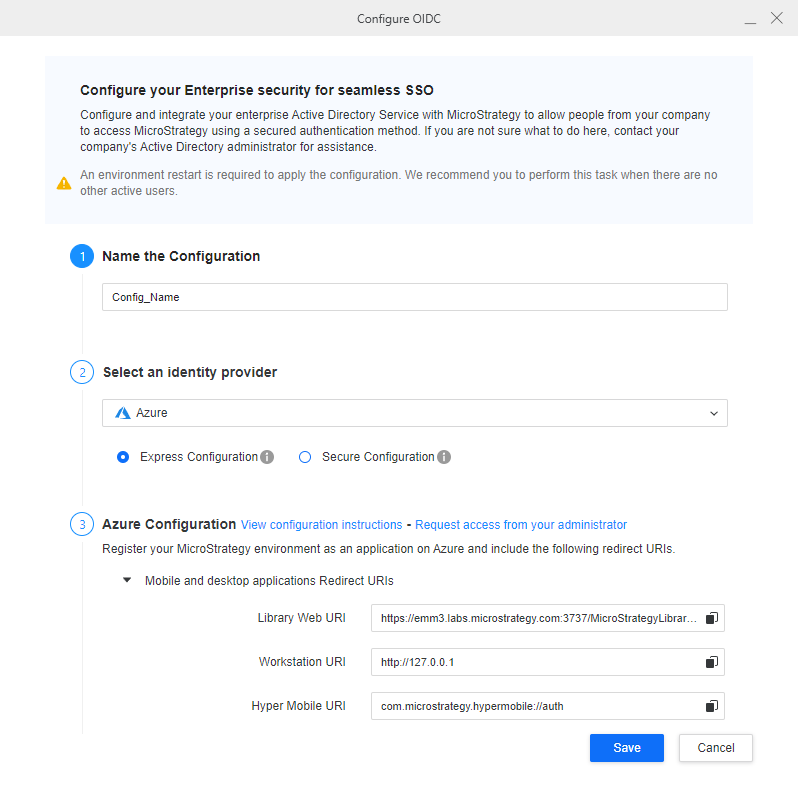
In Name the Configuration/Configuration Name, enter a name for your multi OIDC/SAML configuration to distinguish it from others. The remaining configurations are the same as the server-level settings shown in Enable OIDC Authentication for Strategy Library and Enable Single Sign-On with SAML Authentication.
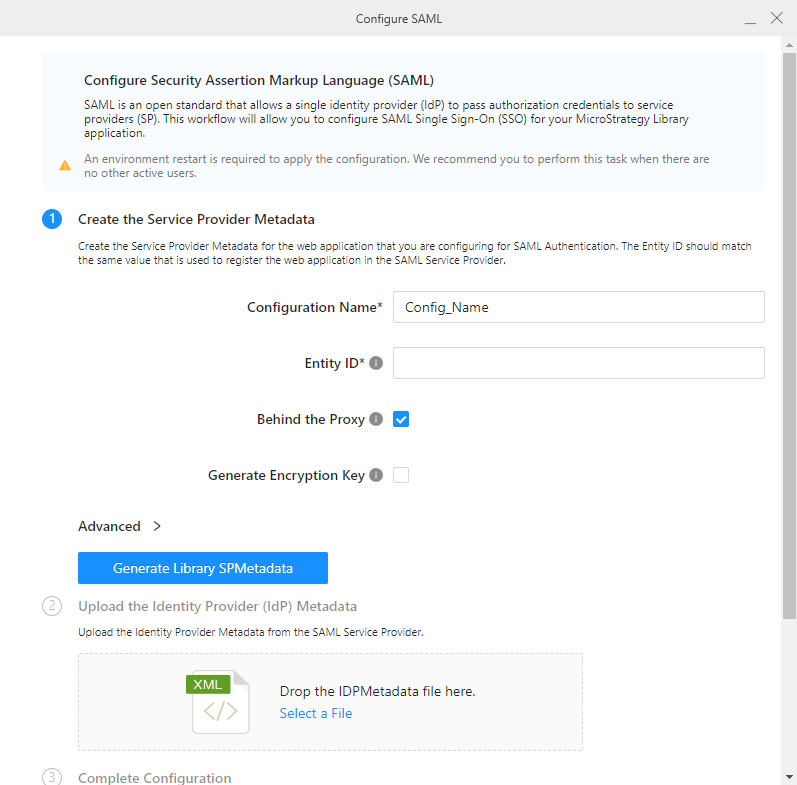
-
When you are finished, confirm the new OIDC/SAML configurations are listed.
Assign Multiple OIDC/SAML Configurations to an Application
-
In the Navigation pane, click Applications.
-
Right-click an application and choose Edit.
-
In Authentication Modes, select Choose specific authentication mods for the app and choose your multi OIDC/SAML configuration for this application.
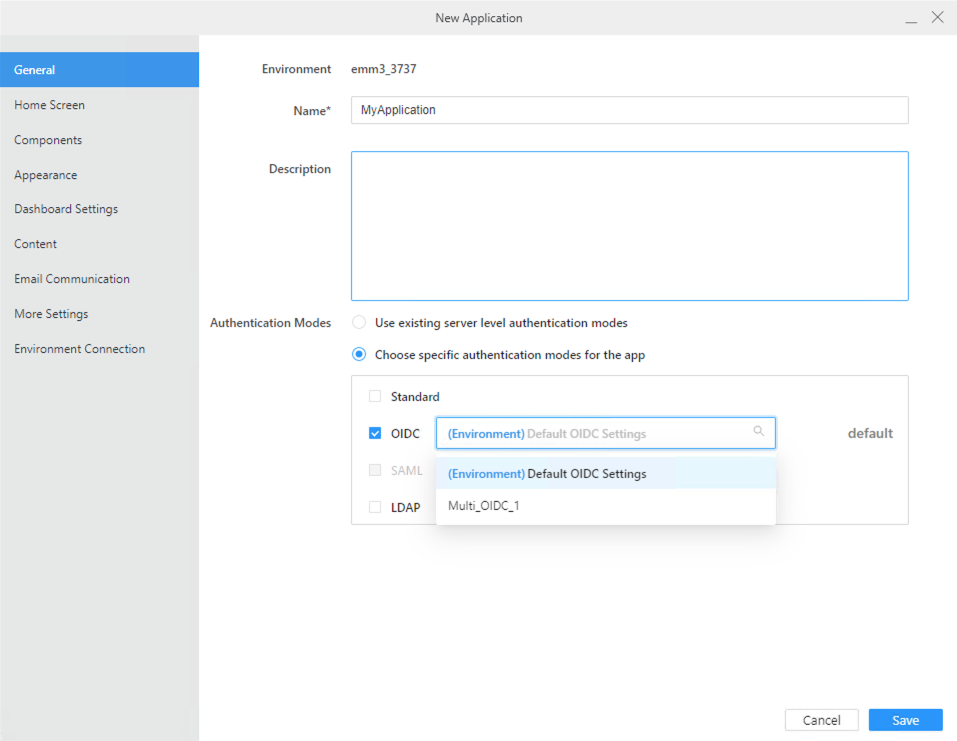
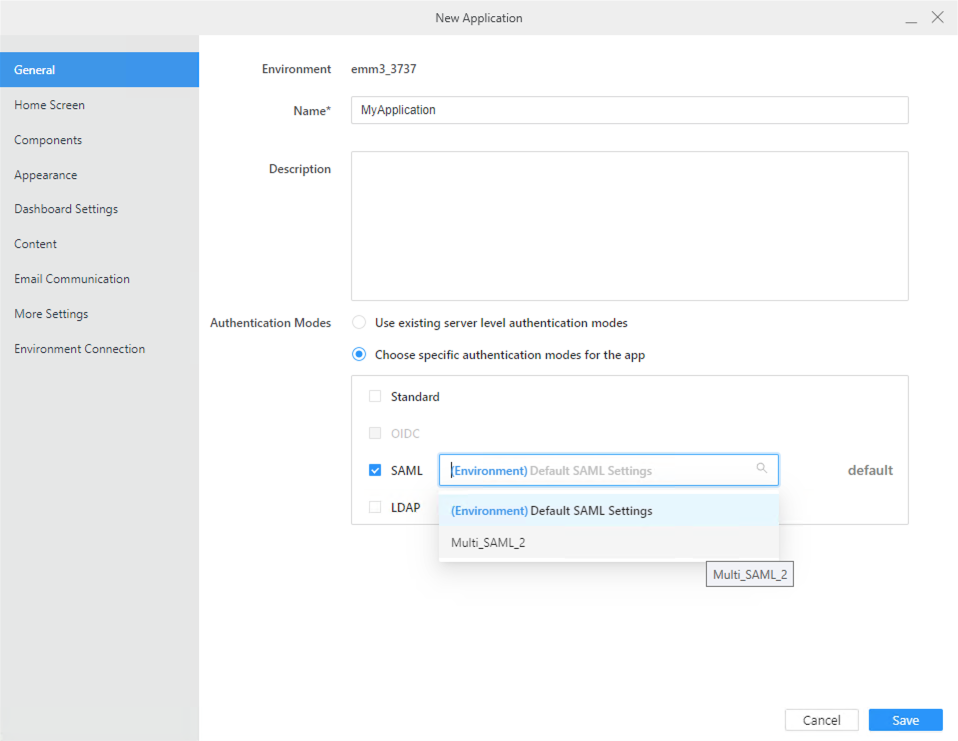
-
Click Save.
Security Setting
Administrators can enable a security setting that mitigates the risk of two individuals from different IDP servers sharing the same name ID.
-
In the Navigation pane, click Enterprise Security.
-
Click System Authentication.
-
Turn on Enable user mapping with SSO configuration.
-
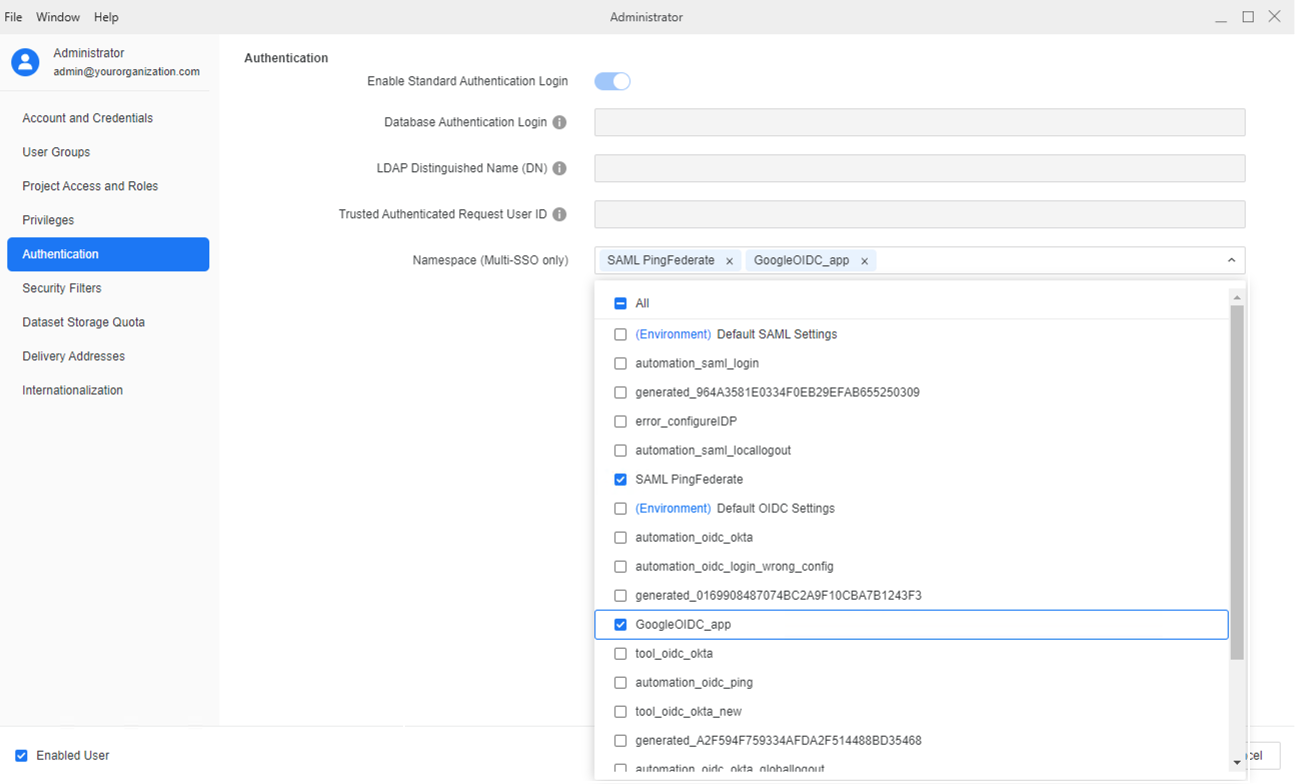
Once this security setting is enabled, navigate to Users & Groups > Edit Specific User > Authentication > Namespace (Multi-SSO only) and select the desired SSO scopes for the user's login. If a user attempts to log in with an SSO scope different than the one configured in the system, the login attempt is rejected.