Strategy ONE
Know When and How to Use the External Security Module
To customize authentication and authorization, the best practice is to use the External Security Module. This Module lets you make use of existing security or an authentication framework, within MicroStrategy Web.
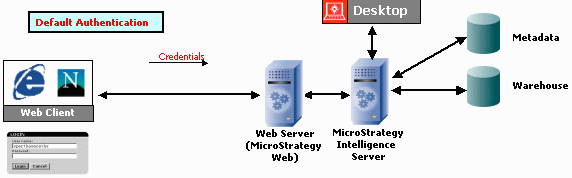
Default login setup: The image below shows the default setup for MicroStrategy Web, without any external security plug-in functionality. Notice the default login form below the Web client:
Answer the following questions to determine whether you should use the External Security Module, and then see the images below for a diagram of your customized implementation:
-
Do you want to use the default login page, or do you want to use a custom, external login page?
-
Do you want to authenticate users against MicroStrategy Intelligence Server, or do you want to perform user-mapping and single sign-on against an external system?
-
Do you want to perform additional checks to determine whether a user is authorized to use the Web application?
Use a custom, external login page. The image below shows how your implementation changes when you customize the application to use a custom, external login page. Notice the customized login form below the Web client:

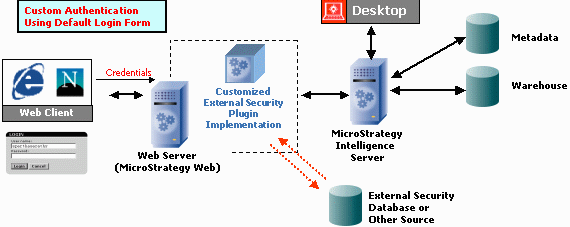
Authenticate against an external system. The image below shows how your implementation changes when you customize the application to authenticate against an external system. This allows you to take advantage of user mapping and single sign-on. (You can use either the default login form as shown in the first image above, or your own custom login form.) Notice the external security database at the bottom of the image:
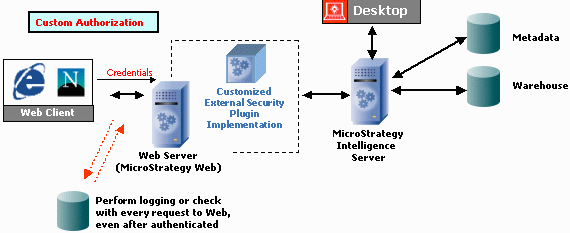
Perform customized user authentication checks. The image below shows how your implementation changes when you customize the application to perform additional user authentication checks. This approach lets you determine whether a user is authorized to use the Web application. Notice the external database at the bottom of the image:
See also:
