Strategy ONE
Single sign-on
Single sign-on allows users to access MicroStrategy Web without having to log in, as a result of having been authenticated by another application. In a typical scenario, when a user connects to MicroStrategy Web, he or she is asked to enter a user ID and password.
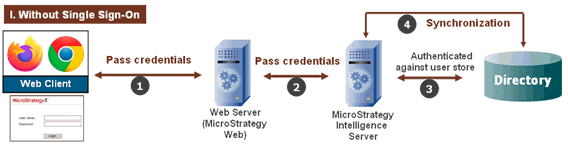
In a single sign-on environment (SSO), the application is protected externally. The only way that a user can gain access to MicroStrategy Web is if they have already been authenticated with an external system. When the user tries to connect to MicroStrategy Web in this environment, the request is intercepted and passed to the third-party SSO provider to authenticate the user. If the user is authenticated and is deemed to have access to the application, the request is then sent to MicroStrategy Web, which understands that the user is authenticated and so simply trusts the user.
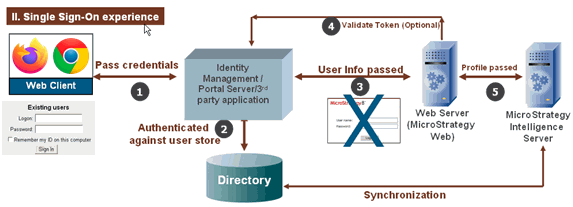
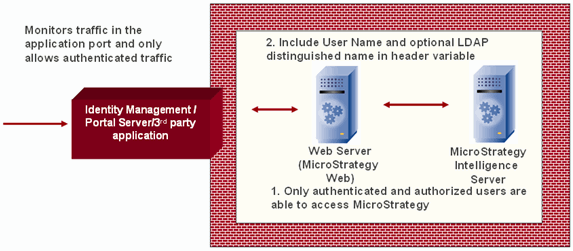
Third-party SSO providers typically monitor the port to which a web application is listening. So, for example, if your web application is listening to port 80, an SSO provider application will monitor all of the traffic on that port and allow through only requests that it has authenticated. SSO providers typically use header variables to pass user information such as the user ID and password and, optionally, the distinguished name (DN). The names of the header variables used to pass the user information will be different depending on the SSO provider being used.
MicroStrategy provides out-of-the-box single sign-on support for the following authentication providers:
-
Windows NT authentication
-
Integrated authentication (Kerberos)
-
Trusted authentication
-
CA Siteminder
-
IBM Tivoli Access Manager
-
Oracle Identity Manager
-
-
Portal authentication
-
Microsoft Office SharePoint
-
Oracle WebLogic
-
IBM WebSphere
-
SAP NetWeaver
-
Liferay
-
DotNetNuke
-
Drupal
-
There are three ways to customize single sign-on to MicroStrategy Web.
-
Customizing trusted authentication
You can use the MicroStrategy Web Customization Editor to customize any of the three supported trusted authentication providers—CA SiteMinder, IBM Tivoli Access Manager, and Oracle Identity Manager. You can also add a new custom trusted authentication provider and customize your MicroStrategy environment to use PHP-based authentication for trusted authentication.
-
Using a custom External Security Module ( ESM)
You can use a custom ESM to customize single sign-on to MicroStrategy Web. For example, you can add code in the ESM that mimics the out-of-the-box trusted authentication (that is, that confirms a user has been successfully logged in by an authentication server and is a valid MicroStrategy user). The Single Sign-on (SSO) Sample illustrates this approach. You can also add code in the ESM to perform other kinds of logic, such as adding additional authorization criteria.
In the Single Sign-on (SSO) Sample, a custom ESM contains the logic to confirm whether or not a user has been successfully logged in by an authentication server and is a valid MicroStrategy user. To accomplish this, the code in the custom ESM class retrieves a token that has been passed in the URL and validates it using the sample authentication server provided as part of this sample. (In a production environment, the token would be validated using the API of the existing authentication server.) If the token is valid, the ESM creates a new MicroStrategy Intelligence Server session and returns the newly created session to MicroStrategy Web. If the token is invalid, the ESM tells MicroStrategy Web to redirect the user to a custom login page.
-
Implementing SSO through a third-party application
You can customize SSO through a third-party application in several ways. You can use a credential mapper class to customize SSO to any of the out-of-the-box MicroStrategy portlets. You can also use the MicroStrategy Task Infrastructure to customize SSO through a third-party application.
