Strategy ONE
Integrate MicroStrategy Mobile with Microsoft Intune in Android
You can use the Microsoft Intune platform to add an extra layer of security to your mobile device and tablet that are running MicroStrategy Mobile or Library. Instructions for integrating MicroStrategy Mobile and Library with Intune are provided below. Please note that this covers integrating the MicroStrategy Mobile and Library SDKs (also known as the AppConfig version of the apps) for Intune or the apps directly from the Google Play Store.
- Prerequisites
- Set Up the Intune Environment
- Optionally, Enable Integrated Authentication for Azure AD Single Sign-On
You can choose the level of security that you want Intune to apply using the Data Loss Prevention when creating App Configuration Policies. For detailed information, refer to your Intune documentation.
- You can enable Data Loss Prevention to protect sensitive data in applications. When you enable this setting, some features are automatically disabled, but you can separately control other actions that involve transmitting data back and forth such as copying and pasting, printing, and taking pictures.
- When you do not enable Data Loss Prevention, you can perform almost every out-of-the-box MicroStrategy Mobile or Library data transfer.
The level of security you choose is determined by the stringency of the security requirements in your environment versus the need for less restrictive data transfer.
To use MicroStrategy Mobile for Android with an EMM provider that supports the AppConfig protocol, you must first meet the following prerequisites:
- You must have an operational EMM system, such as Intune. The instructions in this topic use Intune as the example. Refer to the documentation provided by your EMM provider for a detailed explanation of how to perform the tasks described in these instructions in your environment.
- The Intune console must be registered with a managed service account on Google Play for Work and be configured as your EMM provider.
- Devices must be enrolled with Intune with a work profile and have encryption enabled.
- The app must be added for the enterprise on Google Play for Work and registered as a public app on the Intune Console.
-
If you want to customize MicroStrategy Mobile for Android, you must install the Android development environment and set up the MicroStrategy Mobile project.
It is recommended that you use Android Studio. Consult your Android documentation to ensure that your system meets the Android Studio requirements. To set up the Android development environment, download Android Studio and confirm the following:
- The Android SDK path is correct
- You installed the Android SDK version mentioned in What's New in the Mobile SDK for Android
- You installed JDK 7 or higher
To set up your Intune environment so users can install the MicroStrategy Mobile or Library application with Intune support on their mobile devices, perform the administrative tasks listed below. For a detailed explanation of how to perform these tasks, refer to the Intune Mobile Application Management Guide.
- Register yourself on Intune.
- Distribute the app:
- Using the Google Play Store.
For instructions, see Add Managed Google Play apps to Android Enterprise devices with Intune.
- Using an .apk file.
Internal app (the. apl build from our DMG) is described as an Android line-of-business app, which is uploaded by your administrator.
Once the app is distributed, you can find it in the Apps section of Company Portal on your device. You can choose to install the app on your device.
For instructions, see Add an Android line-of-business app to Microsoft Intune.
- Using the Google Play Store.
- Set security policies and configurations within the Intune Console, depending on your requirements.
In Intune we can create configurations and restrictions with App configuration policies and assign them to app and user groups. For Android, the configurations can only be set for apps from Google Play Store (Android Work). The configurations can be set by the JSON editor or by the key-value configuration editor.
To set the configurations with the key-value configuration editor:
- In Intune, choose the Client apps workload.
- Choose App configuration policies in the Manage group, and choose Add.
- Set the following details:
- Name - The name of the profile that appears in the Azure portal.
- Description - The description of the profile that appears in the Azure portal.
- Device enrollment type - Choose Managed devices for devices that have been enrolled in Intune.
Select Android for Platform.
Choose Associated app to choose the app for which you want to define an app configuration policy. Select from the list of Managed Google Play apps that you have approved and synchronized with Intune.
Select Permissions. It's recommended to use the configuration editor to set your configurations.
The screenshot below has the configurations loaded from the Google Play Store. These configurations (i.e. manifest restrictions) were defined in app_restrictions.xml of the app, and can be loaded into Intune for configuration (in the middle of the screenshot).
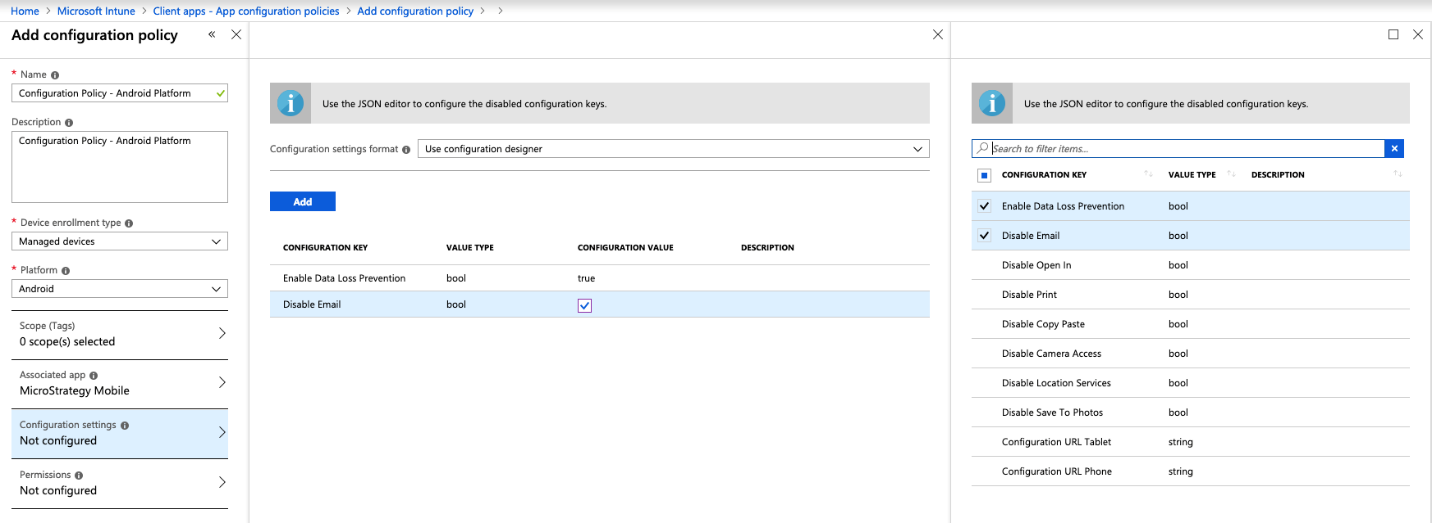
For more information, see Add app configuration policies for managed Android Enterprise devices.
- Add the users and devices in your organization that are allowed to use the mobile application.
To assign these policies to users to specific users or groups, select the users from the assignments tab in Intune.
- In Intune, select Client Apps.
- In the Manage section, select Apps. Select the app you want to assign.
- In the Manage section, select Assignments.
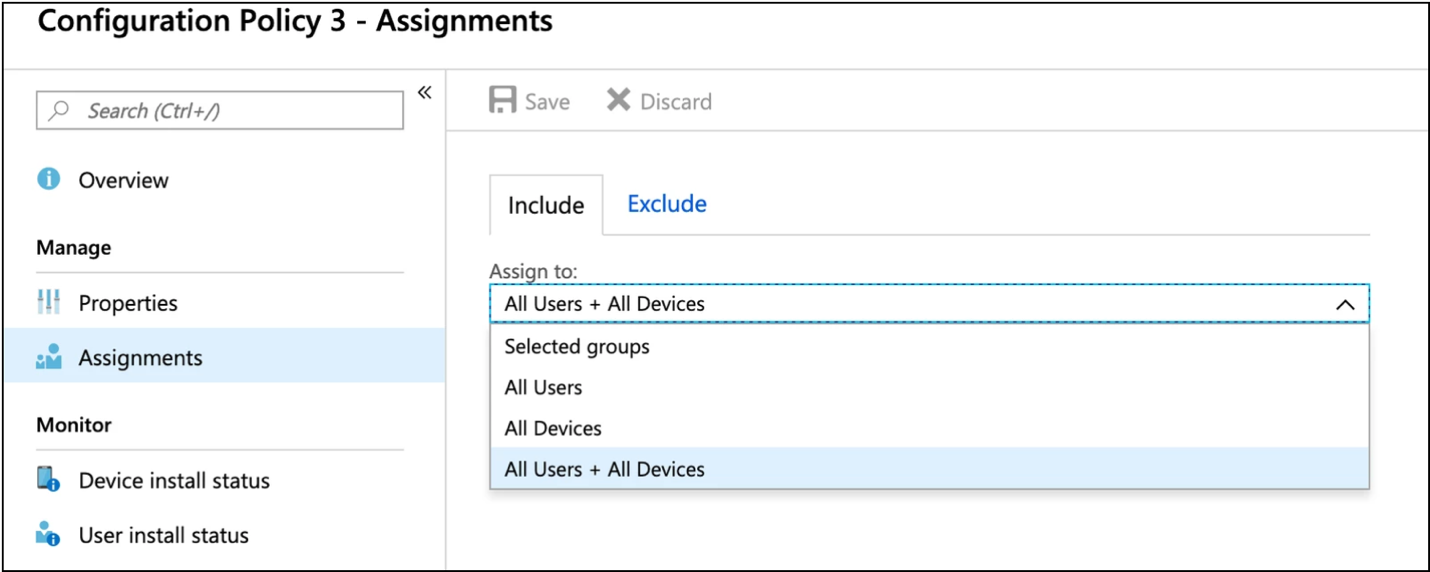
- Select Add Group to open the Add group pane that is related to the app.
For the specific app, select an assignment type:
- Available for enrolled devices: Assign the app to groups of users who can install the app from the Company Portal app or website.
- Available with or without enrollment: Assign this app to groups of users whose devices are not enrolled with Intune. Users must be assigned an Intune license.
- Required: The app is installed on devices in the selected groups. Some platforms may have additional prompts for the end user to acknowledge before app installation begins.
Uninstall: The app is uninstalled from devices in the selected groups if Intune has previously installed the application onto the device via an "Available for enrolled devices" or "Required" assignment using the same deployment. Web links cannot be removed after deployment.
If you deploy an Android app as Available with or without enrollment, reporting status will only be available on enrolled devices.
For more information, see Assign apps to groups with Microsoft Intune.
- Install the Intune Company Portal on devices.
In order to use the MicroStrategy mobile and Library Apps with Intune, the Intune Company Portal must be downloaded from the Google Play Store on each device where the app is deployed. Upon logging into Intune, users may be prompted to enable a Management profile on the device so that the MicroStrategy app can be managed by Intune.
For more information, see Enroll Android devices.
-
Configure Per-App VPN
- Create VPN profiles. For instructions, see Create VPN profiles in Intune.
- In Intune, select Client apps > Apps.
- Select an app from the list > Assignments > Add group.
- In the Assignment type, select Required or Available for enrolled devices.
- Select Included Groups > Select groups to include > Select the group you created > Select.
- In VPNs, select the per-app VPN profile you created.
- Save your changes.
Optionally, Enable Integrated Authentication for Azure AD Single Sign-On
For information, see KB483178.
