Strategy One
Integrate Strategy with Okta OIDC Single Sign-On
Starting in MicroStrategy ONE (December 2024), you can use the Denodo JDBC driver to implement OIDC Single Sign-On with Okta.
Configure Your Application in Okta
Create an Okta Application
- Log in to Okta.
- In the Navigation pane, under Applications, click Applications.
- Click Create App Integration.
- Choose the OIDC - OpenID Connect sign-in method and the Native Application application type.
- Click Next.
- Enter a name for the application integration, and choose the Refresh Token and Token Exchange grant types.
- Add your sign-in redirect URIs for your environment, for example,
https://env-308750.customer.cloud.microstrategy.com/MicroStrategyLibrary/auth/oidc/login. - Choose the Allow everyone in your organization to access controlled access.
- Click Save.
Create an API
- In the Navigation pane, under Security, click API.
- Click Add Authorization Server.
- Enter a name and audience and click Save.
- Navigate to the Scopes tab of your newly created API.
-
The scope name should be the same as the role name in the database. Denodo scopes are the same name as roles. Once Denodo has the scopes of the token, it obtains roles with the same names and executes the request with the privileges granted to these roles.
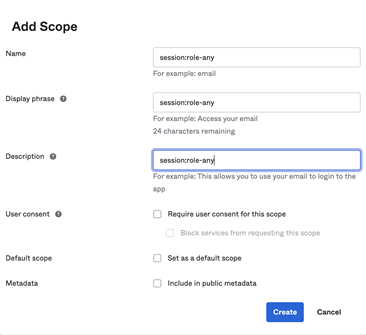
- Click Create.
Create an Access Policy and Rule
- Navigate to the Access Policies tab of your newly created API.
- Click Add Policy.
- Enter a name and description. Optionally, customize Assign to.
- Click Create Policy.
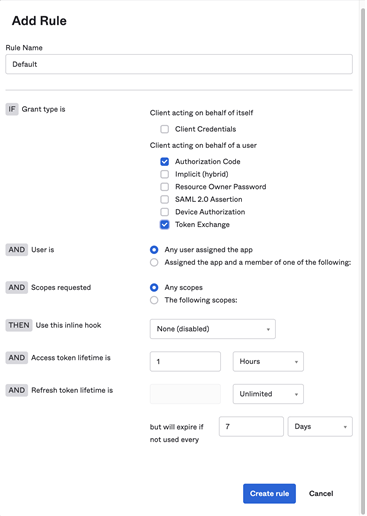
- Click Add rule.
- Enter your preferred rule options and click Create rule.
- Click Actions and Edit.
- In Assign to, assign the rule to the application you created.
- Click Update Policy.
Integrate Denodo with Okta
For more information on enabling OAuth in Denodo, follow the instructions in the JWT section of Enabling OAuth Authentication.
-
Open the Denodo Administration Tool and log in with an Administrator account.
-
In the menu, click Administration and Server configuration.
-
Click Server authentication and OAuth.
-
Define the following values:
-
Select a validation mode: Select Use JWT.
-
Select the signing algorithm: Choose RS256.
-
Issuer: Use the value from your OpenID configuration. To find this value, use
https://<okta_url>.okta.com/oauth2/<serverid>/.well-known/oauth-authorization-server. -
JWKS URL: Use the value from your OpenID configuration. To find this value, use
https://<okta_url>.okta.com/oauth2/<serverid>/.well-known/oauth-authorization-server. -
Audience: Enter your Okta Authorization Server Audience value.
To find this value in Okta, in the Navigation pane, under Security, click API, and copy the Authorization Server Audience value.
-
Scope field name: Type
scp.
-
-
Click OK.
-
To create roles in Virtual DataPort and grant them the appropriate privileges, see Creating Roles.
The role name is used in Add Scope in Okta.
Strategy Configuration
Create a Data Source Using OIDC Single Sign-On Authentication Mode
-
Open the Workstation window.
-
Connect to an environment.
-
Create an IAM object using Manage OAuth Enterprise Security with Identity and Access Management (IAM) Objects.
-
Use the Client ID and Client Secret from your Okta application.
-
In Scope, enter
openid email profile offline_access <scope created>, where<scope created>is the scope name from Create an API.
-
-
In the Navigation pane, click
 next to Data Sources.
next to Data Sources. -
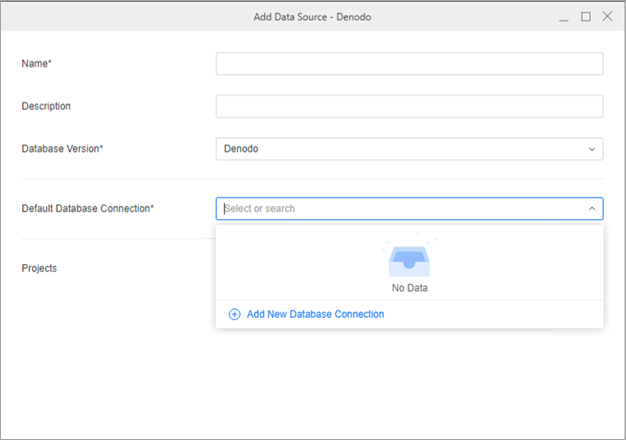
Search for and choose Denodo from the data source list.
-
In the Default Database Connection drop-down list, click Add New Database Connection.
-
Type a Name.
-
In the Driver drop-down list, choose the Denodo JDBC driver.
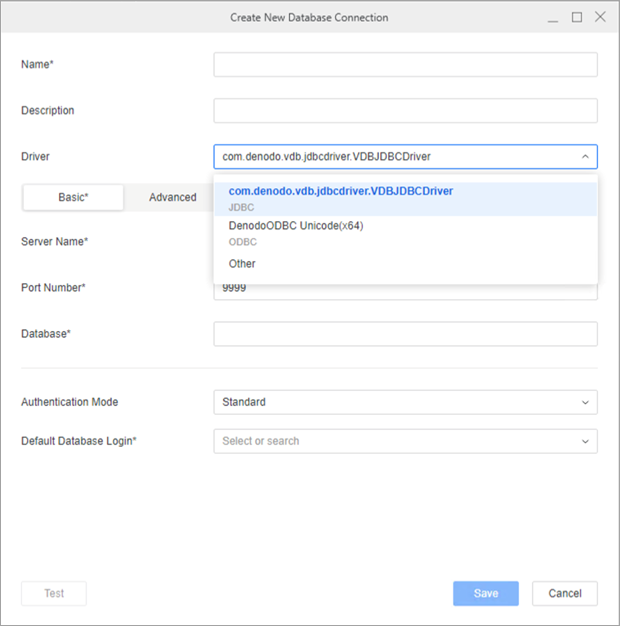
-
Type a Server Name, Port Number, and Database.
-
In the Authentication Mode drop-down in the Basic tab, choose OIDC Single Sign-On.
-
In the Authentication Service drop-down list, choose the authentication service you created above or click Add New Authentication Service.
For more information on creating Identity and Access Management objects, see Manage OAuth Enterprise Security with Identity and Access Management (IAM) Objects.
-
Click Save.
-
In the Add Data Source dialog, enter a Name and Database Version, and optionally choose Projects for further data manipulation.
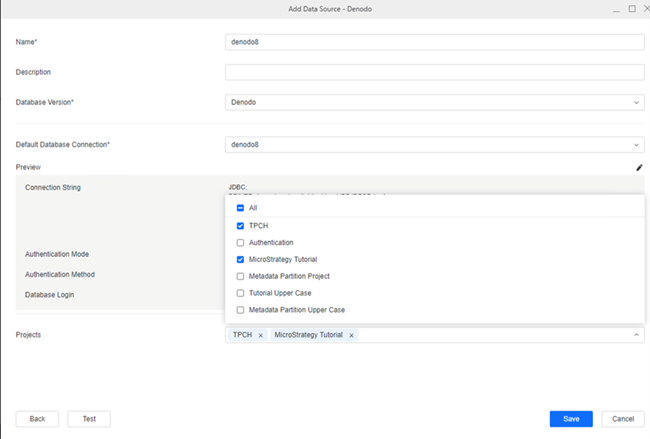
-
Click Save.
Create and Map Users to Okta
-
Open the Workstation window.
-
Connect to an environment.
-
In the Navigation pane, click Users and Groups.
-
Click
 next to All Users.
next to All Users.
-
Type a Full Name, Email Address, Username, and other optional fields.
-
In the left pane, click Privileges and select the check box next to the following privileges:
-
Access data from Databases, Google BigQuery, Big Data, OLAP, BI tools
-
Create and edit database instances and connections
-
Create and edit database logins
-
Create configuration objects
-
Create dataset in Workstation
-
Configure project data source
-
Monitor Database Connections
-
Use Workstation
-
-
In the left pane, click Authentication.
-
In Trusted Authentication Request User ID, type the Okta user's email address.
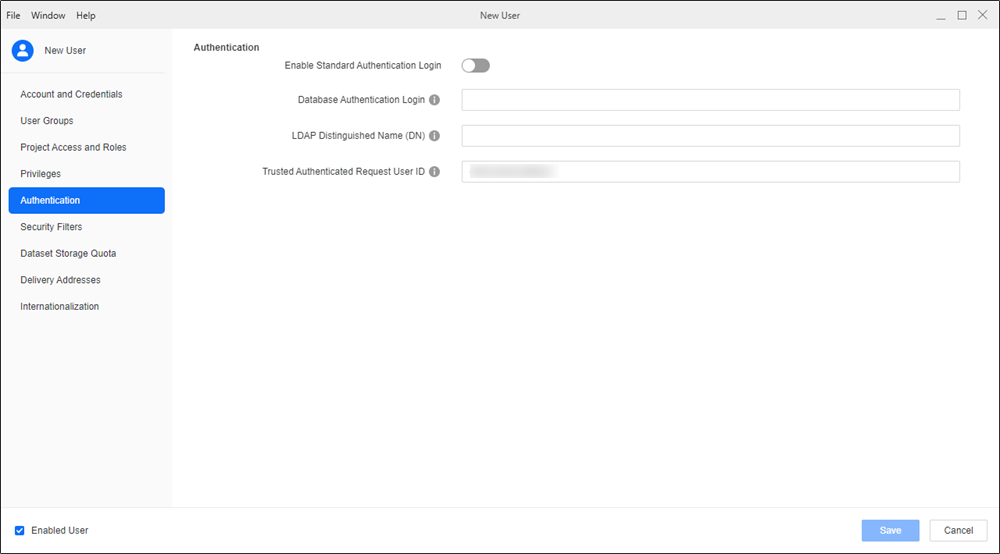
-
Click Save.
Configure OIDC
For more information, see Enable OIDC Authentication for Strategy Library.
-
Open Workstation and connect to your environment using standard authentication and administrator credentials.
-
Right-click the connected environment and choose Configure OIDC under Configure Enterprise Security.
-
In Step 2: Select an identity provider, choose Okta from the drop-down list.
-
Copy the Strategy Library URI and Workstation URI into the mobile and desktop application's sign-in redirect URIs in the Okta application you created in Create an Okta Application.
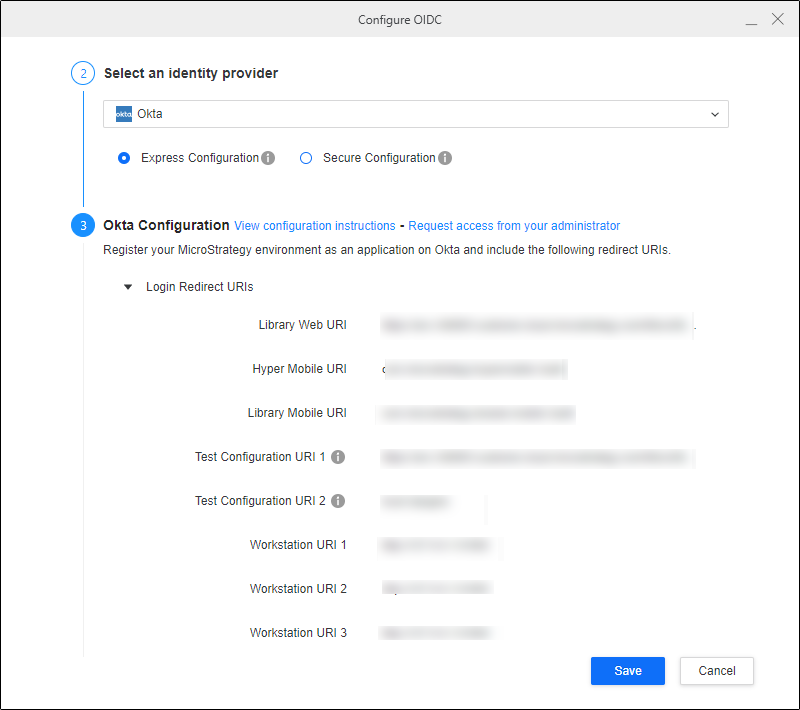
-
Copy and paste the Client ID of the application you created in Create an Okta Application.
-
Use the Issuer value from Okta. To find this value, use
https://<okta_url>.okta.com/oauth2/<serverid>/.well-known/oauth-authorization-server. -
Click Save.
-
Restart the web server.
Single Sign-On with OIDC
-
Open the Workstation window.
-
Connect to an environment.
-
Right-click the environment and choose Environment under Edit.
-
Select Default OIDC and click Continue.
-
A browser displays. Log in using your Okta credentials.
-
Use a Strategy Administrator account to assign privileges to the new user.
You do not need to perform this step if you mapped a Strategy user to an Okta account and granted privileges.
-
In the Navigation pane, click
 next to Datasets.
next to Datasets. -
Choose a Project and select Data Import Cube.
-
Click OK.
-
Choose the data source you created in Create a Data Source Using OIDC Single Sign-On Authentication Mode.
The namespaces and tables display.
