Strategy ONE
Configure SameSite Cookies for MicroStrategy Web and MicroStrategy Mobile
The information in this topic applies to MicroStrategy Mobile, as well as MicroStrategy Web.
Starting in MicroStrategy 2021 Update 7, you can manage SameSite cookies for MicroStrategy Web and Mobile in the MicroStrategy Web and Mobile Administrator pages, respectively. See Configure the SameSite Flag for MicroStrategy Deployments for managing SameSite cookies in MicroStrategy 2021 Update 6 and older.
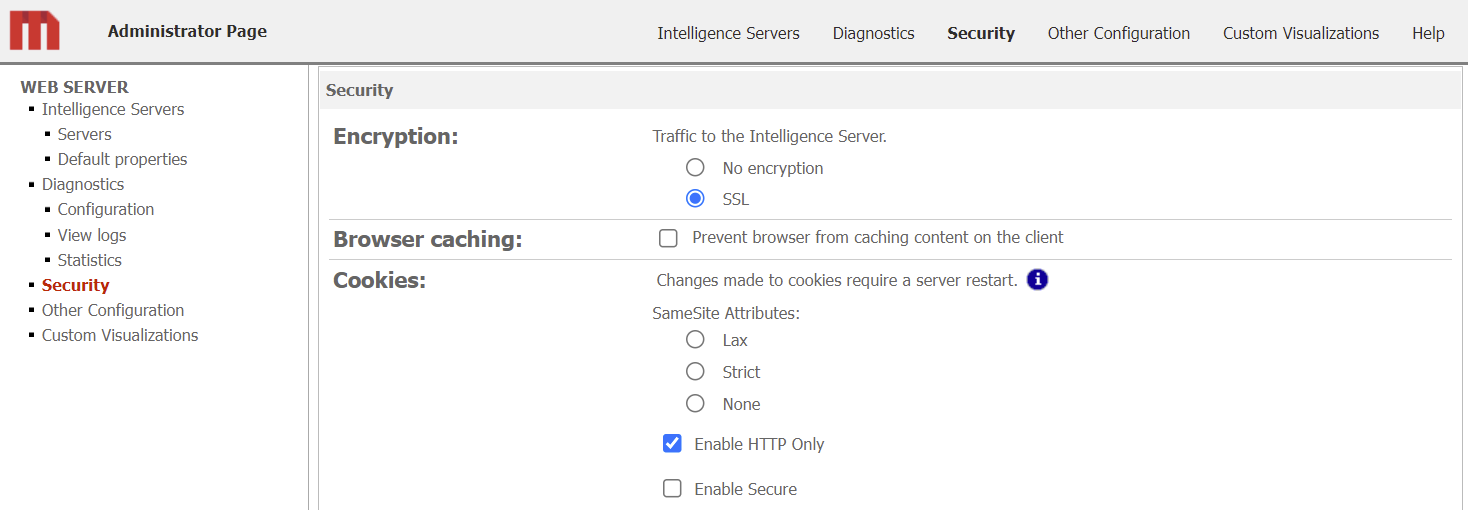
SameSite prevents the browser from sending cookies along with cross-site requests. The main goal is to mitigate the risk of cross-origin information leakage. It also provides protection against cross-site request forgery attacks. Possible values are as follows:
-
Lax Provides a reasonable balance between security and usability for websites that want to maintain user’s logged-in session after the user arrives from an external link. The default option for SameSite is Lax, including when no option is selected.
-
Strict Prevents the cookie from being sent by the browser to the target site in all cross-site browsing contexts, even when following a regular link.
-
None Allows cookies in all cross-site browsing contexts.
An HTTPS connection is a prerequisite for the None selection. If the SameSite cookie attribute is set to None, the associated cookie must be marked as Secure.
A SameSite attribute of None is recommended in the following scenarios:
-
There are cross-domain compatibility issues.
-
MicroStrategy Web and MicroStrategy Library are deployed in a domain other than the one displayed in the user's address bar.
-
You are using Security Assertion Markup Language (SAML), OpenID Connect (OIDC,) and third party authentication.
The cookie flag changes vary depending on your server:
Due to application server limitations, settings in the user interface only apply to the JSESSIONID cookie on Tomcat application servers.
Tomcat Web and Mobile Servers
-
Access the MicroStrategy Web Administrator page. (How?)
-
In the left pane, select Security.
-
Based on your requirements, select the appropriate SameSite attribute. The SameSite attribute is unselected by default.
-
Click Save and restart the Web server.
IIS Web and Mobile Servers
The application server must support the SameSite cookie changes. Upgrade the .NET Framework to v4.8 and make sure that the latest updates have been applied. See KB articles that support SameSite in .NET Framework on the Microsoft Docs site for more information.
-
Navigate to
C:\Program Files (x86)\MicroStrategy\Web ASPx\web.config. -
Create a backup of
web.config. -
in
web.config, add the parameters shown below.In the
<sessionState />tag, addcookieSameSite="None"In the
<httpCookies />tag, addsameSite="None" -
Contact your IT team to configure and enable SSL and apply the necessary certificates on the IIS server.
-
Go to the SSL Settings and select Require SSL.
-
Restart the IIS Web server.
WebLogic Web and Mobile Servers
-
Access the MicroStrategy Web Administrator page. (How?)
-
In the left pane, select Security.

-
Based on your requirements, select the appropriate SameSite attribute and click Save. The SameSite attribute is unselected by default.
-
In the MicroStrategy deployment, navigate to
MicroStrategy\WEB-INF\weblogic.xml. -
Edit
weblogic.xmland add the code shown below.Copy<session-descriptor>
<cookie-path>/;SameSite=NONE</cookie-path>
<cookie-secure>true</cookie-secure>
</session-descriptor> -
Click Save and restart the Web server.
JBoss Web and Mobile Servers
Setting Samesite as None for the JSessionID cookie is only supported by JBoss 7.3.3 and newer. The following procedure was tested using JBoss 7.3.7.
-
Access the MicroStrategy Web Administrator page. (How?)
-
In the left pane, select Security.

-
Based on your requirements, select the appropriate SameSite attribute and click Save. The SameSite attribute is unselected by default.
-
In JBoss, navigate to
jboss/standalone/configuration/standalone.xml. -
Edit
standalone.xmland add<session-cookie http-only="true" secure="true"/>to the existing code as shown below.Copy<subsystem xmlns="urn:jboss:domain:undertow:10.0" default-server="default-server" default-virtual-host="default-host" default-servlet-container="default" default-security-domain="other" statistics-enabled="${wildfly.undertow.statistics-enabled:${wildfly.statistics-enabled:false}}">
<buffer-cache name="default"/>
<server name="default-server">
<http-listener name="default" socket-binding="http" redirect-socket="https" enable-http2="true"/>
<https-listener name="https" socket-binding="https" security-realm="ApplicationRealm" enable-http2="true"/>
<host name="default-host" alias="localhost">
<location name="/" handler="welcome-content"/>
<http-invoker security-realm="ApplicationRealm"/>
</host>
</server>
<servlet-container name="default">
<jsp-config/>
<session-cookie http-only="true" secure="true"/>
<websockets/>
</servlet-container>
<handlers>
<file name="welcome-content" path="${jboss.home.dir}/welcome-content"/>
</handlers>
</subsystem> -
Create a new file named
undertow-handlers.confusing the code shown below and save it to theWEB-INFfolder of the MicroStrategy Web/Mobile deployment.Copysamesite-cookie(mode=NONE) -
Restart the Web server.
