Strategy One
This page applies to MicroStrategy 2021 Update 4 and newer versions.
Use Signed Authn Requests for SAML in MicroStrategy 2021 Update 4
In the MicroStrategy 2021 Update 4 SAML workflow, there’s a change to the Spring Security SAML project for the signature. Follow the steps in this topic if your setup meets following the conditions:
-
Your SAML works correctly prior to MicroStrategy 2021 update 4. No change is done on IdP side.
-
After migrating the same configuration files to 2021 Update 4 environments, the SAML redirection is normal.
-
After entering the SAML user name and password in the login page, the login fails.
Troubleshooting
Check the SAML response network trace. If you see the following response and there’s no assertion appended, follow the solution below.
urn:oasis:names:tc:SAML:2.0:status:ResponderSolution
In IdPMetadata.xml, add WantAuthnRequestsSigned="true".
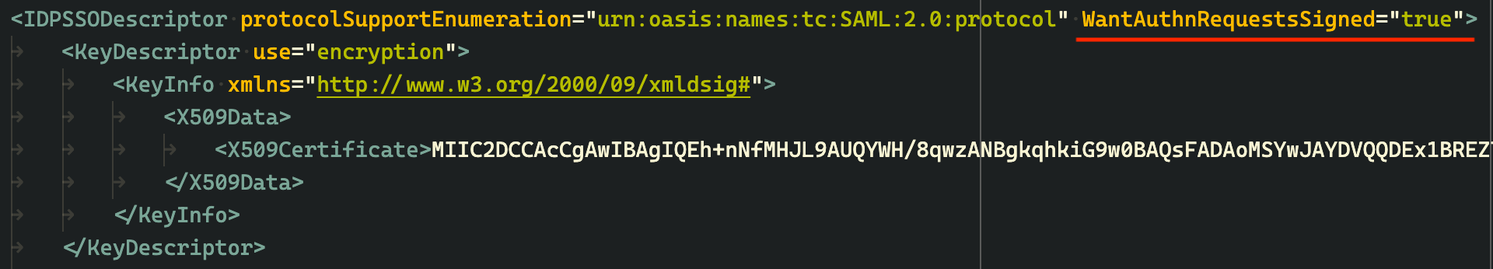
MicroStrategy has encountered one ADFS case where this parameter is a must-have for SAML to work properly.
