Strategy ONE
Add Certificate Pinning for iOS
Certificate pinning strengthens the normal security provided by HTTPS. In particular, making it difficult for a malicious server to carry out a man-in-the-middle attack. HTTPS simply checks to see if a certificate in the certificate chain for the server exists in the trust store on the mobile device. However, certificate pinning compares the public key for the Library server with the same public key bundled into MicroStrategy Library on the mobile device.
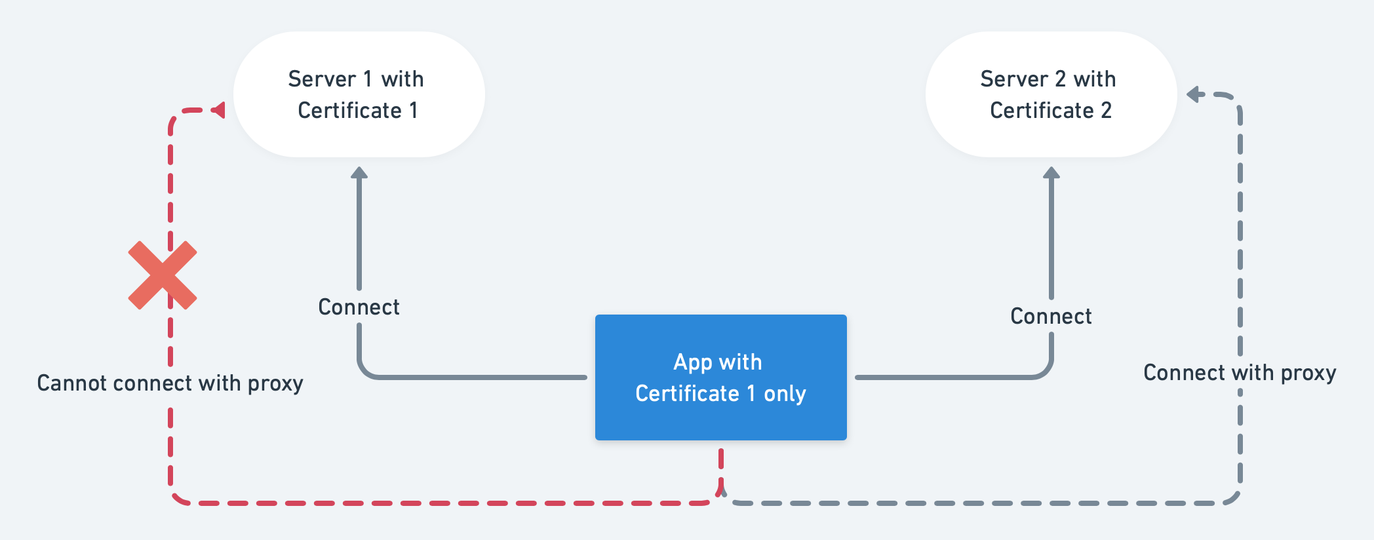
With certificate pinning configured, end users cannot connect a certified server with proxy as shown in the image below with server 1. However, they can still connect an uncertified server directly or with proxy, as shown in the image below with server 2.
Like any other application contacting a server, when a MicroStrategy Library application attempts to connect to a Library server, it first performs the standard HTTPS certificate verification. If the HTTPS verification is successful, MicroStrategy Library checks to see whether it should verify that Library server is a trusted server. It does this by looking in Finalbundle.bundle to see if there are any certificates in a folder with the name of the Library server. If it finds a certificate, it compares the hash of the public key in that certificate with the hash of the public key in the certificate on the Library server. If the hashes match, the connection is allowed. If there are no certificates in the folder with the name of the Library server, the connection is allowed by passing the standard HTTPS certificate verification.
The MicroStrategy Library implementation of certificate pinning follows the IETF certificate pinning guidelines. In addition to minimizing the risk of a man-in-the-middle attack, certificate pinning has the advantage that it continues working even if the certificate for the Library server changes—for example, it expires. There is no need to recompile the MicroStrategy Library app since the public key itself has not changed, only the certificate. There is also support for multiple certificates for a single Library server. This allows you to create a backup certificate for a Library server, without deploying it, and bundle that certificate in MicroStrategy Library. If your existing certificate is compromised, the backup certificate can be deployed and your app can keep working.
- Open the MicroStrategyLibrary project in Xcode.
-
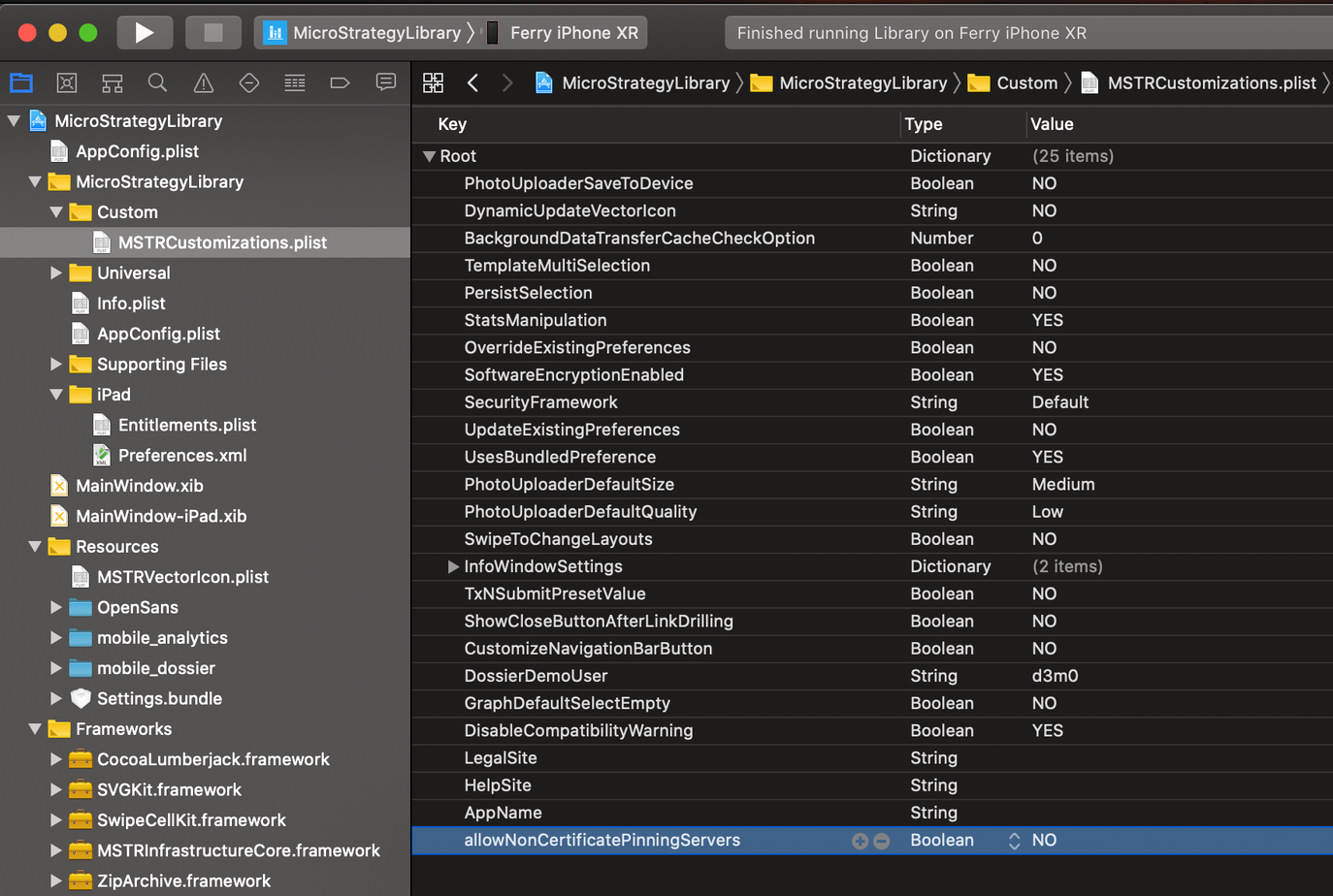
Open MSTRCustomizations.plist. Set allowNonCertificatePinningServers to YES.
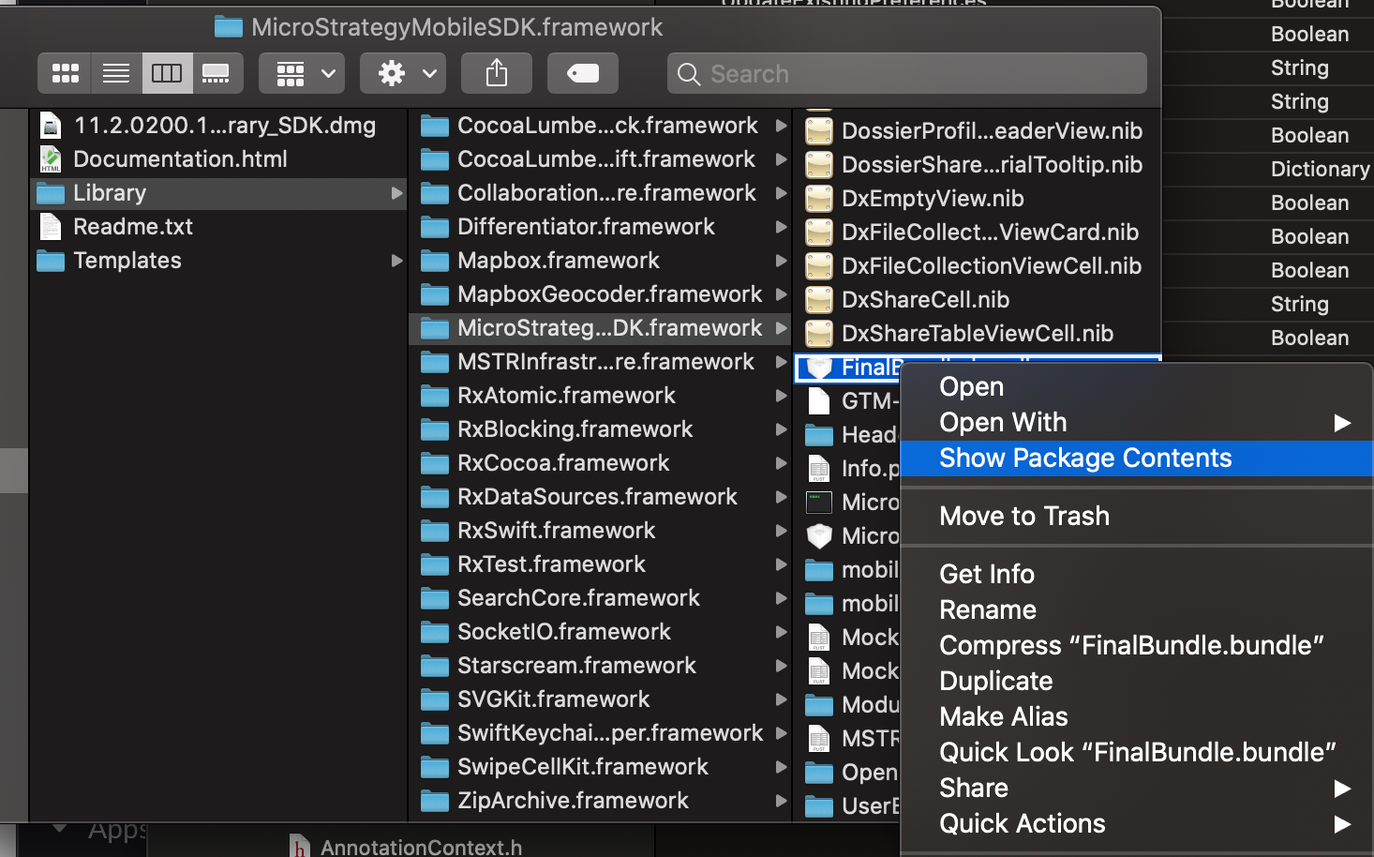
- In the Library folder, navigate to MicroStrategyMobileSDK.framework > FinalBundle.bundle.
-
Right-click FinalBundle.bundle and choose Show Package Contents.
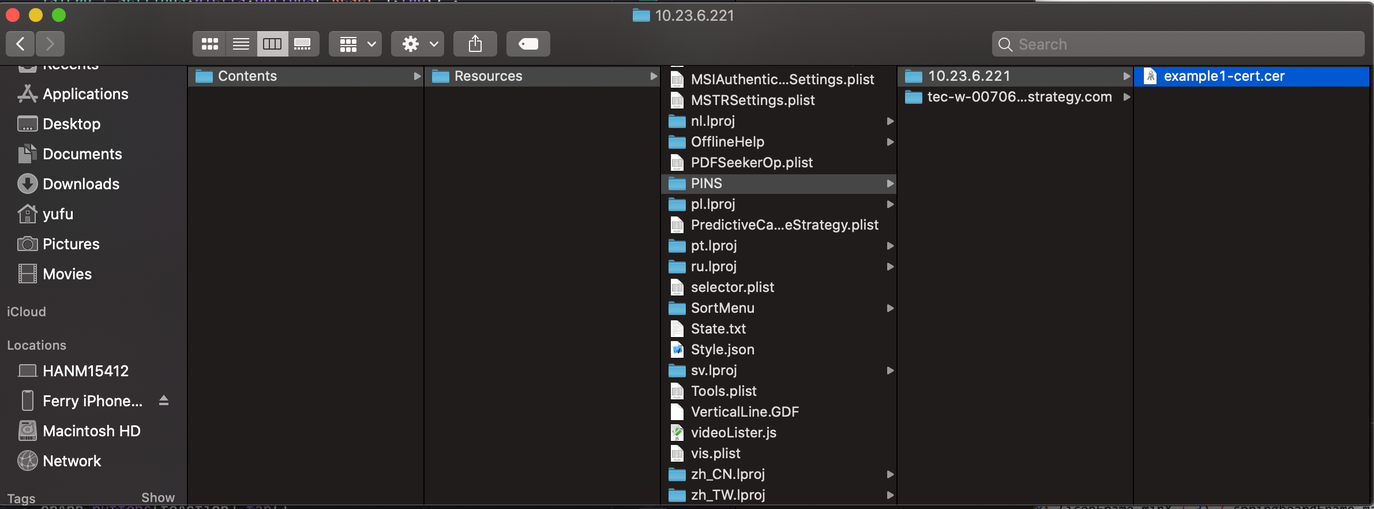
- Navigate to the Resources folder and create a PINS folder.
- Under the PINS folder, add a separate folder for each Library server that you want the Library application to trust. The name of the folder should be the fully-qualified name of the LIbrary server—for example, myMobileServer1.myDivision.myCompany.com.
-
In each Library server folder, add the .cer or .pem certificates that should be trusted when MicroStrategy Library tries to connect to that server.
- Compile the application and deploy it to users.
