Strategy One
Enable Cross Account Bucket Access Using the Amazon S3 Cloud Connector
Prior to MicroStrategy 2021 Update 6, the implementation of the Amazon S3 Cloud connector doesn’t support x-accounts or foreign bucket listings, even when the IAM user used to create the DBRole has the required access privilege.
Starting in MicroStrategy 2021 Update 6, you can enable an IAM user with the required access privileges to access data stored in buckets tied to a different AWS account through Strategy. This feature enhances the Cloud Object Connector to solve problems in the following cases:
-
There are multiple AWS accounts. For example, Account A, Account B, and Account C in an organization (a customer) that uses the Cloud Object Connector to access Amazon S3.
-
There is an IAM user, for example, User A, in Account A, configured to access some buckets in its own account (Account A), as well as some buckets in other accounts (Account B and Account C).
-
There is an Amazon S3 data source created with User A's IAM credentials in the Cloud Object Connector. In the folder browsing workflow of this data source, one can only see buckets from Account A and no Account B or Account C buckets appear.
With this feature, buckets from Account A, plus buckets from Account B and Account C, which User A has access to, is shown in folder browsing.
According to this AWS article, there are three ways to enable Amazon cross-account access:
-
AWS Identity and Access Management (IAM) policies and resource-based bucket policies
-
IAM policies and resource-based Access Control Lists (ACLs)
-
Cross-account IAM roles
The solution implemented by Strategy only works if the account is set up using the first method described above: AWS Identity and Access Management (IAM) policies and resource-based bucket policies.
An Advanced Settings option can be found with a field to add Foreign Account Buckets under Amazon S3 IAM DBRole creation. This feature is accessible on the following Strategy platforms:
-
Web
-
Library
-
Workstation on Mac
-
Workstation on Windows
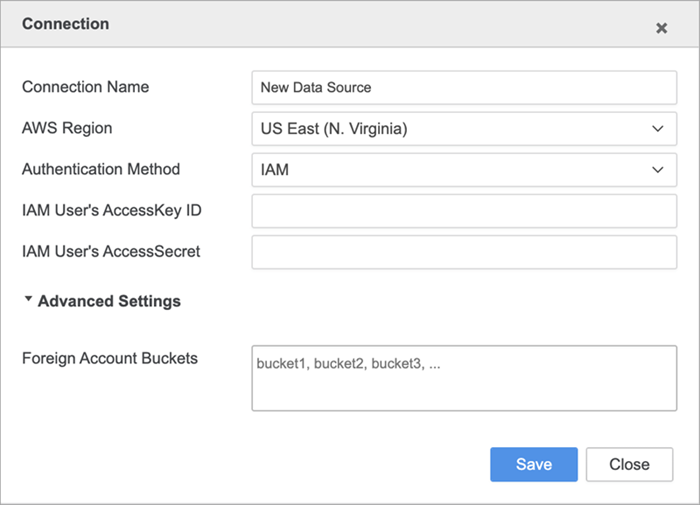
Foreign Account Bucket
Note the following about foreign account buckets:
-
If no foreign account bucket is mentioned, the Amazon IAM workflow works as expected.
-
You can pull in data from local and foreign buckets to create a cube and dashboard.
-
The ‘Foreign Account Bucket’ field follows the same rules as Amazon buckets.
-
Bucket names mentioned must be between 3 (min) and 63 (max) characters long.
-
Bucket names listed can consist only of lowercase letters, numbers, dots (.), and hyphens (-).
-
Bucket names listed must begin and end with a letter or number.
-
Bucket names listed must not contain two adjacent periods.
-
Bucket names listed must not be formatted as an IP address (for example, 192.168.5.4).
-
Bucket names listed must not start with the prefix, xn--.
-
Bucket names listed must not end with the suffix, -s3alias.
-
The field does not accept duplicates. If any duplicates are mentioned, they are automatically removed and only one copy of the name is saved.
-
The field accepts a maximum of 1000 characters at a time.
-
Bucket names listed must be unique across all AWS accounts in all the AWS Regions within a partition.
-
-
For a DBRole created, if the user doesn't have the listAllBucket privilege and no foreign bucket is mentioned, then the following error is returned.
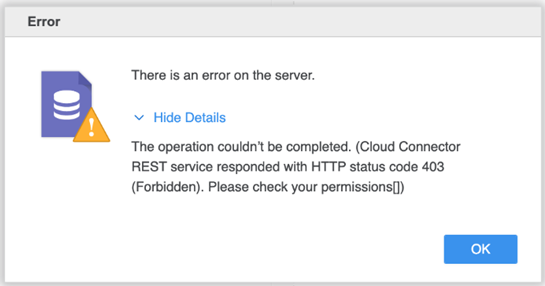
Create a DBRole with a Foreign Account Bucket
-
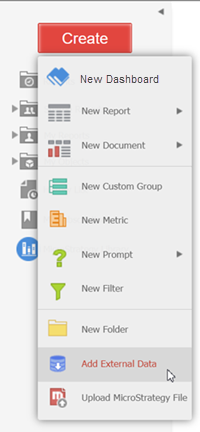
In Strategy Web, click on the Create button > Add External Data.
-
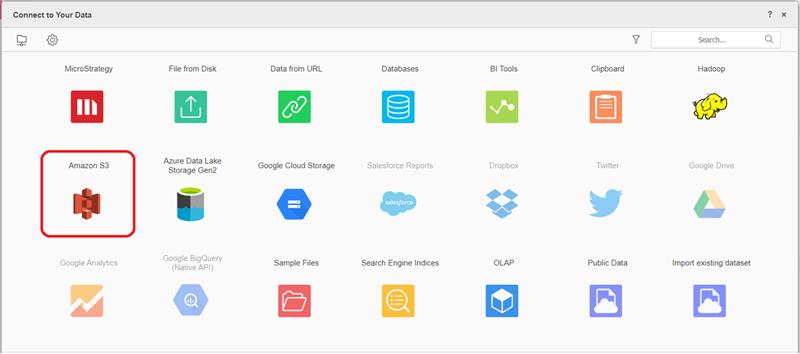
Find and select the Amazon S3 Cloud Object connector from the data source list.
-
Next to Data Sources, click New Data Source
 to add a new connection.
to add a new connection. 
-
Enter your connection credentials:
- Connection Name: A name for the new connection.
- IAM User's AccessKey ID: The access key ID.
- IAM User's AccessSecret: The secret access key.
- Advanced Settings > Foreign Account Buckets: List of foreign buckets (separated by commas) that the user and credentials have access to.
-
Click Save.
-
Select the newly created DBRole and scroll through the list of buckets in the Available Files panel to see the foreign buckets.
