Strategy One
Azure Data Lake Storage Gen2 User OAuth Connectivity
Learn to configure Azure Data Lake Storage OAuth connectivity with Entra ID (formerly Azure AD).
Azure Administrator Configuration
The following section refers to the configuration steps on Azure for the User OAuth workflow.
Create and Configure the Application
- Go to the Microsoft Azure Portal and authenticate.
-
Navigate to Entra ID.
-
From the left menu, click App registrations.
- Click the New Registration menu.
-
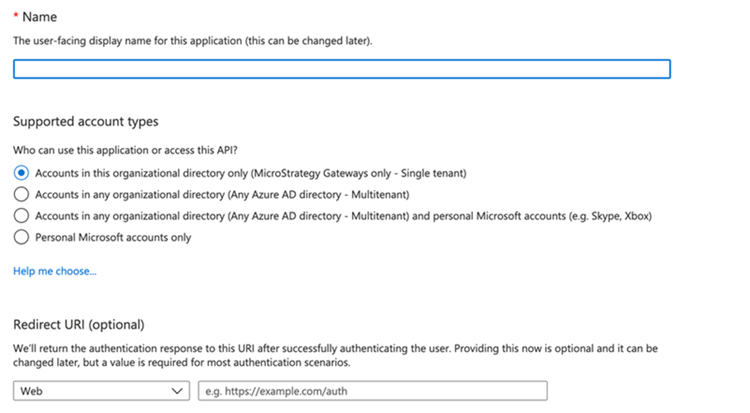
Complete the following required information.
- Name: Provide a name for your application.
- Supported account type: Select the Account is the organizational directory only (Microsoft Gateways only - Single tenant) option.
-
Redirect URI: Provide the redirect uri for your application. For Strategy, it is the URL used to deploy Strategy Web. For example, https://host:8443/MicroStrategy/servlet/mstrWeb?evt=3172, where the host is the IP for your Strategy Web host.
- Return to the App Registration page and find the registered app under the Owned Applications section.
-
Click on the app > API permissions.
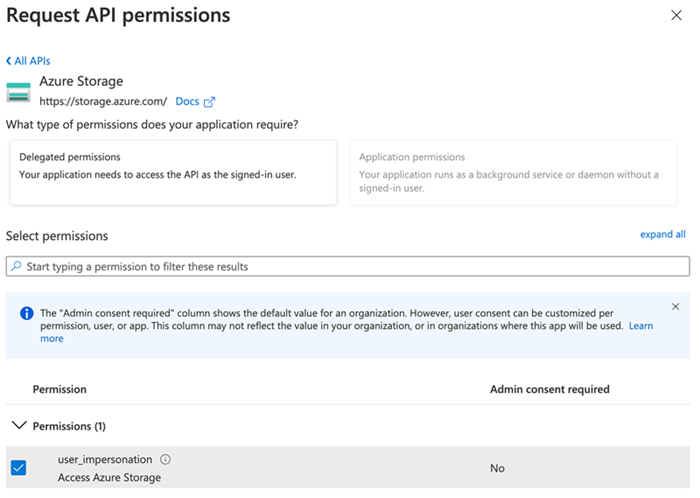
- In the dialog, click Add a permission > Azure Storage.
-
Expand Permissions and select the user_impersonation checkbox.
Configure User Permission
Grant permission to the Azure Active Directory user so that they can read Azure Storage content.
- Go to the account that will be accessed by users.
-
From the left menu, click Access Control (IAM) > Role assignments.
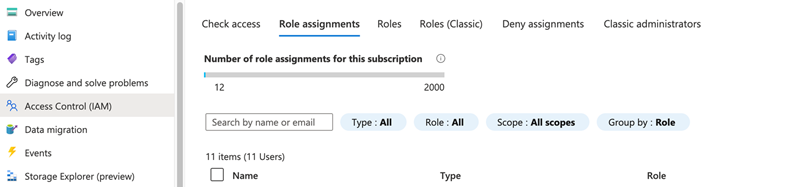
- In the upper left, click Add.
-
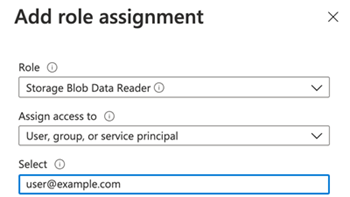
In the Add role assignment dialog, complete the required fields.
- Role: Select the Storage Blob Data Reader option.
- Assign access to: Select User, group, or service principal option.
-
Select: Enter the user account you want to allow access to this storage account via User OAuth.
Collect Connection Information to Create a Database Role
The following parameters are required to access Azure Database Lake Storage via User OAuth authentication.
|
Parameter Name |
Description |
How to Find it |
|---|---|---|
|
Tenant ID |
The Tenant ID of your Azure Active Directory. |
Azure Portal > Azure Active Directory service |
|
Client ID |
The ID of the application registered in Create and Configure the Application. |
Azure Portal > Azure Active Directory service > App Registrations, click on your registered app |
|
Client Secret |
The secret of the application registered in Create and Configure the Application. |
Upon app registration, a secret is generated. To generate a new secret, go to your app > Manage > Certificates & secrets, click New client secret |
|
Azure Storage Account |
The storage account you added permission to for your Azure Active Directory user. |
|
|
Callback URL |
The URL that is invoked after user login. For StrategyWeb, it is https://host:8443/MicroStrategy/servlet/mstrWeb?evt=3172, where the host is your web’s IP or hostname. |
