Strategy ONE
Linux Install Wizard - Topology Configuration
Topology allows administrators to monitor Strategy services and manage them in Strategy Workstation. The following functionality is supported:
-
Service Health Monitor
The administrator can monitor Strategy services through Workstation and visualize if they are running or stopped.
-
Service Start/Stop
The administrator can start or stop Strategy services through Workstation. This functionality is currently limited to SSH authentication with username and password.
See View Environment Toplogy and Monitor Services in the Workstation Help for more information about using topology within Workstation.
The two following types of lightweight agents are used to monitor services in Workstation:
-
Monitoring Agents
The monitoring agents come with the installation of most Strategy services. Use them to monitor services and view their health status.
-
Communication Agents:
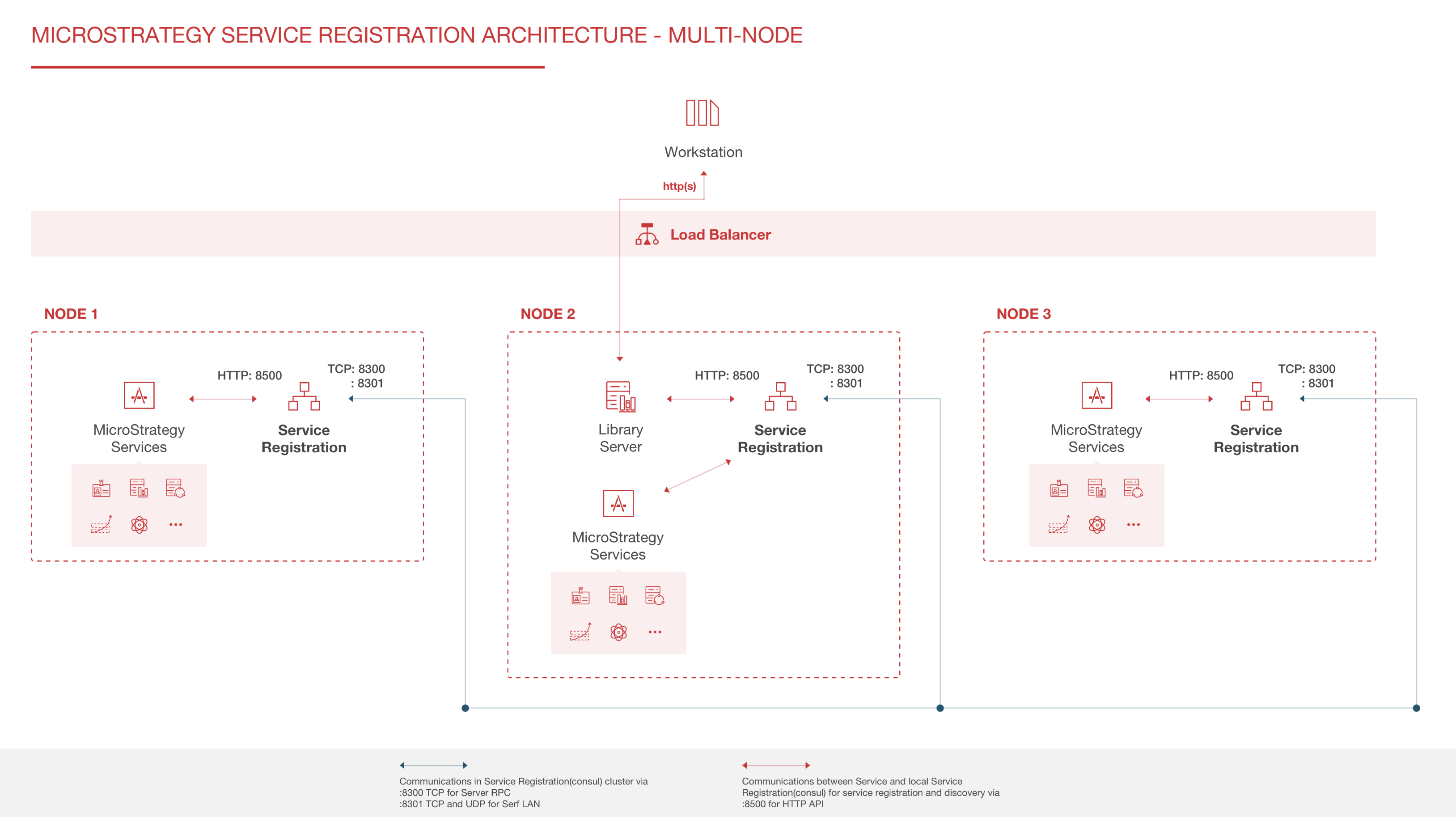
Some monitoring agents also act as communication agents. In addition to monitoring services, communication agents help other monitoring agents locate each other and gather monitoring information. The administrator must pick at least one agent to act as a communication agent, so all other agents can locate each other through this agent.
On environments where three or more machines host Strategy Services, it is recommended that you choose at least three communication agents to provide redundancy and improved reliability, in case one communication agent becomes unavailable. The machines chosen to act as communication agents must be machines that host Strategy Services, such as Intelligence Server or Strategy Library. If you decide to use only one communication agent, it is recommended that you choose the machine that houses Strategy Library (if deployed through the Strategy installation), since Library communicates directly with Workstation.
If your Library deployment is done through a WAR file or if you do not use a machine that houses Strategy Library to host the communication agent, then use a machine that houses Intelligence Server.
Strategy One uses Consul technology for Services Registration. A monitoring agent corresponds to a Consul agent in client mode. A communication agent corresponds to a Consul agent in server mode.
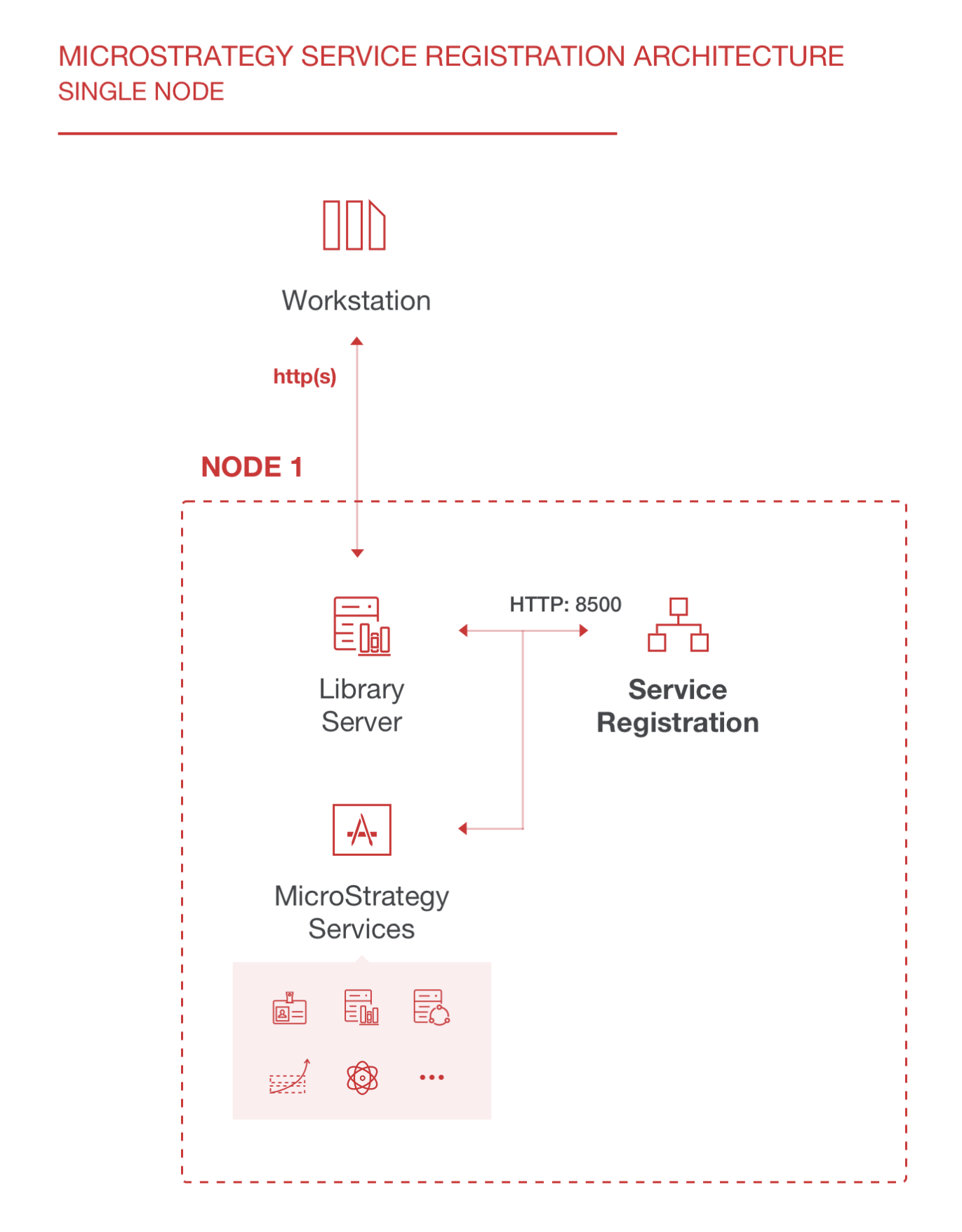
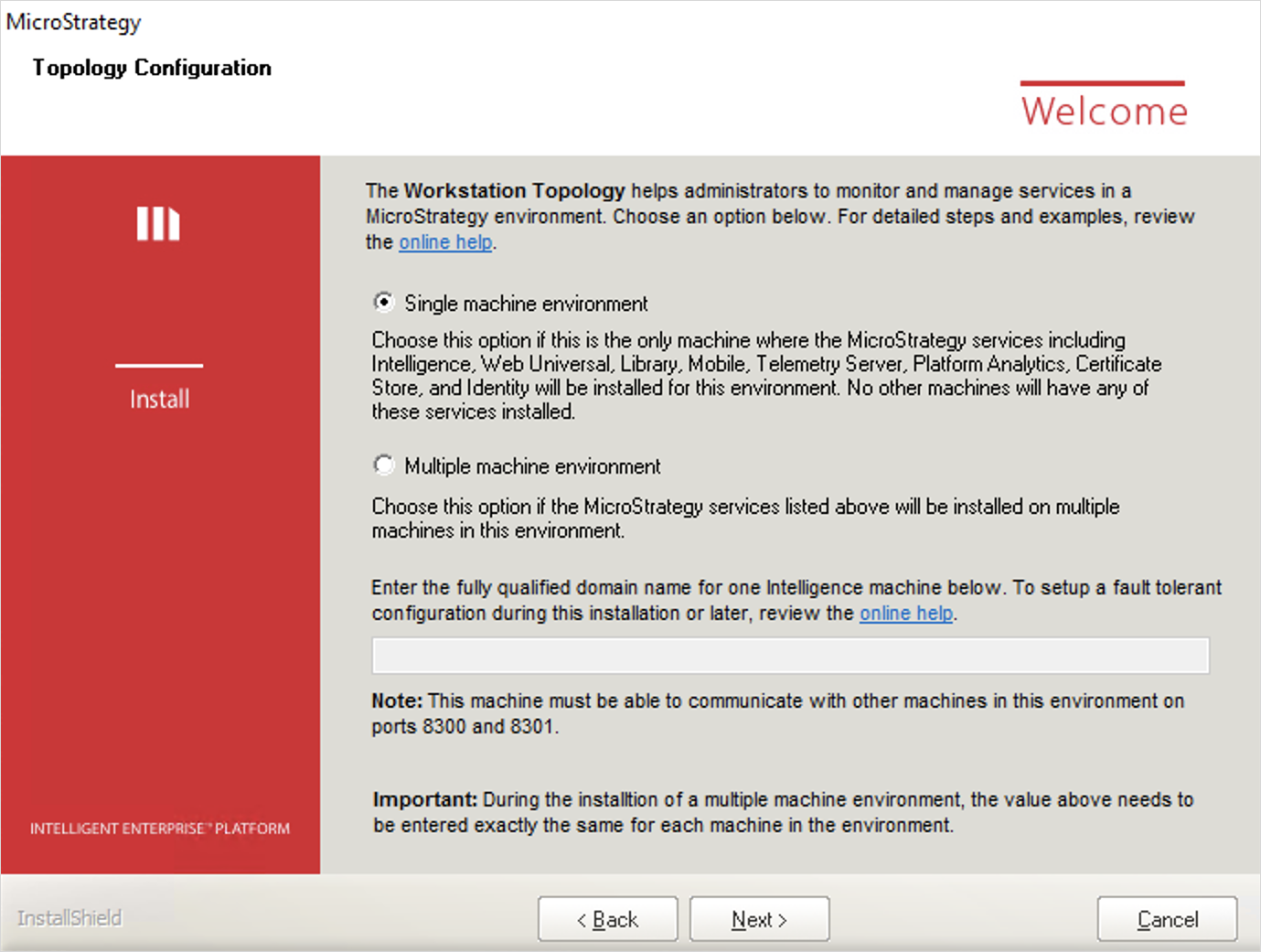
- On the Topology Configuration dialog of the Installation wizard, select whether your environment has Single or Multiple machines.
-
If your environment contains multiple machines, determine which machines in your environment you want to act as communication agents. Among all the machines in your environment that will host Strategy Services, select at least one of them (three are recommended for multiple machine environments) to act as a communication agent. Enter each machine in the text field, separated by semicolons. You must input the exact same list on all machines, using the Topology Configuration dialog of the Installation wizard, including the monitoring and communication agent machines.
The Strategy Services are as follows:
- Strategy Intelligence Server
- Strategy Web Universal
- Strategy Library
- Strategy Mobile
- Strategy Messaging Services
- Strategy Platform Analytics
- Strategy Certificate Store
An odd number of communication agents is required due to the leadership selection algorithm.
Examples:
Copyservername1.domain.com;servername2.domain.com;servername3.domain.com;
servername1.domain.com;Example: Your environment contains the following two machines and you select one machine to host the communication agent:
- Machine 1 hosts Strategy Library and the communication agent
- Machine 2 hosts the Intelligence Server
When performing the installation, enter the full domain name, machine1.domain.com, on both machines.
Example: Your environment contains the following three machines and you want all machines to host a communication agent:
- Machine 1 hosts Strategy Library
- Machine 2 hosts Intelligence Server 1
- Machine 3 hosts Intelligence Server 2
When performing the installation, enter machine1.domain.com;machine2.domain.com;machine3.domain.com; on all three machines.
Example: Your environment contains the following five machines and you select three machines to host the communication agents:
- Machine 1 hosts Strategy Library
- Machine 2 hosts Intelligence Server 1 and a communication agent
- Machine 3 hosts Intelligence Server 2 and a communication agent
- Machine 4 hosts Intelligence Server 3 and a communication agent
- Machine 5 hosts Intelligence Server or other services
Enter machine1.domain.com;machine2.domain.com;machine3.domain.com; on all machines.
Some important information to keep in mind:
-
In MicroStrategy 2019, OpenSSH is no longer installed on Windows machines. You must install Open SSH to start and stop services using topology. Upgrading your system from 11.0 to 2019 removes Open SSH.
If consul is already installed on a machine, prior to installing Strategy One products, the service registration auto configuration and execution is affected. We do not recommend a separate consul installation on the same machine.
- If you select Multiple machine environment, you must enter an odd number of machines.
- If your environment includes more than one machine and machines with dynamic IP addresses as communication agents, use FQDN for the communication agent machine list during the installation.
- If your environment includes more than one machine and machines with more than one IP address as communication agents, it is recommended that you use FQDN for the communication agent machine list during the installation. If IP address list is used, make sure the machine with multiple IP addresses can be pinged with an IP address included in the list.
Topology supports installation on machines with public IP addresses. To avoid unexpected joins to topology nodes, possibly exposing service information, you must configure your firewall correctly. Your firewall should allows ports for Server RPC (default 8300), and Serf LAN (default 8301), and Serf WAN (default 8302) only for the nodes within the Workstation topology node cluster. See Enabling Topology Communication Through a Firewall for more information.
After installing the topology feature, see Installing and Configuring Topology for additional instructions on configuring this feature to work in your environment.
