Strategy One
Configure Key Pair Authentication
Strategy One (July 2025) adds support for key pair authentication using Google Secret Manager, HashiCorp Cloud, and HashiCorp Vault.
Starting in Strategy One (June 2025), you can use key pair authentication to connect to Snowflake.
Prerequisite
See the following sections in the Snowflake Key-Pair Authentication documentation:
-
Generate the private key
-
Generate a public key
-
Assign the public key to a Snowflake user
-
Verify the user's public key fingerprint
Your key-pair can be encrypted or non-encrypted.
Private Key Fetch Method
Decide a method to store your private key. Strategy supports the following methods:
-
Upload the private key from a local client machine
If you are using an ODBC connection, you must use this method.
-
Store private key content in AWS Secrets Manager and Azure Key Vault
Upload from a Local Client Machine
-
Copy your private key files to a local directory to store.
-
Note the path to the files.
-
If you are using encrypted key pairs, note the passphrase.
Store Private Key Content in a Credential Manager
Strategy supports maintaining private key content using a third party credential manager for Snowflake JDBC connections only. Therefore, users can manage their own key rotation schedule. Strategy can easily fetch key content from the third party credential managers while the connection is established. To utilize this private key, create a data source in Workstation and then use the connection across all platforms.
AWS Secret Manager
Create a secret in AWS Secret Manager. For more information, see Create an AWS Secrets Manager Secret.
For an encrypted key, in Key/value pairs, click Add row and add the following key/value pairs:
-
usernameand<insert username> -
private_key_pwdand<insert private-key-password> -
private_key_base64and<insert private-key-content-base64>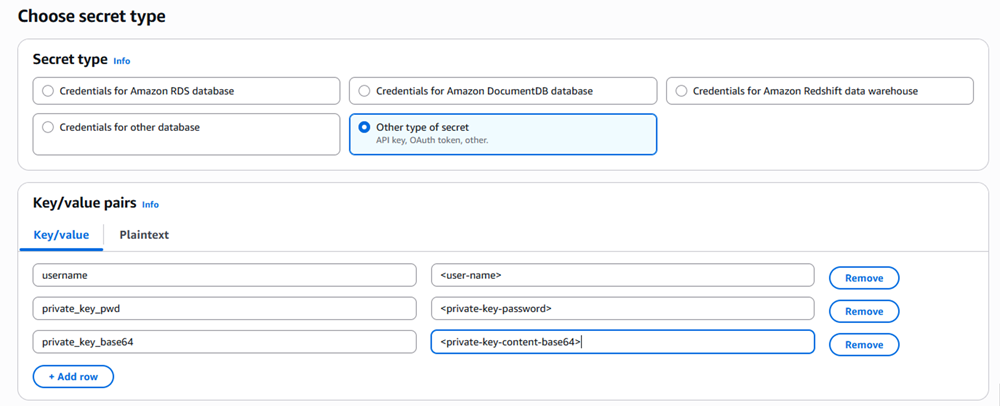
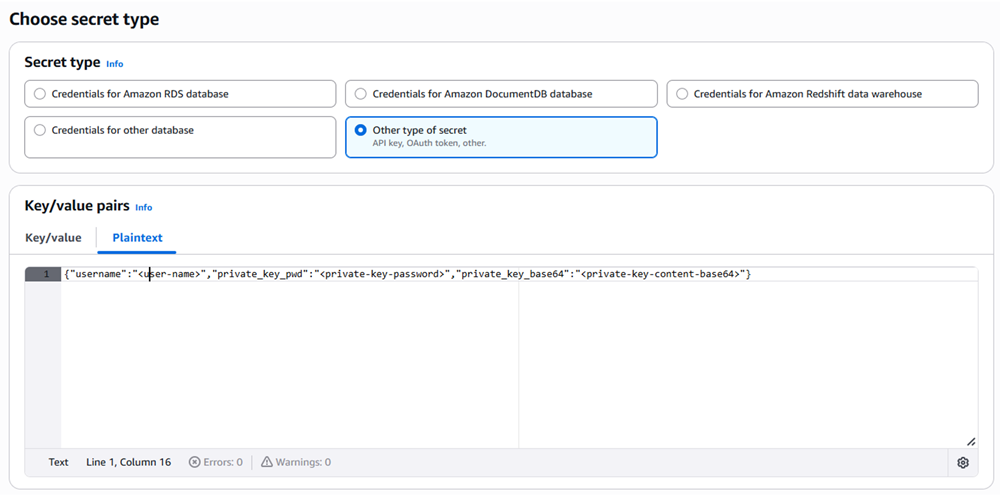
You can also create the Key/values pairs if you go to Plaintext and paste the following text, replacing the values specific to your details:
{"username": "<user-name>", "private_key_pwd": "<private-key-password>", "private_key_base64": "<private-key-content-base64>"}
For a non-encrypted key, in Key/value pairs, click Add row and add the following key/value pairs, replacing the second value with your details:
-
usernameand<user-name> -
private_key_base64and<private-key-content-base64>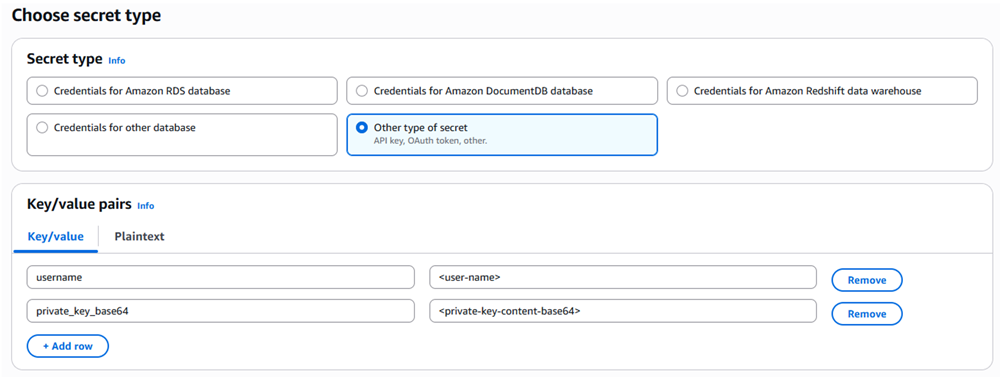
You can also create the Key/values pairs if you go to Plaintext and paste the following text, replacing the values specific to your details:
{"username": "<user-name>", "private_key_base64": "<private-key-content-base64>"}
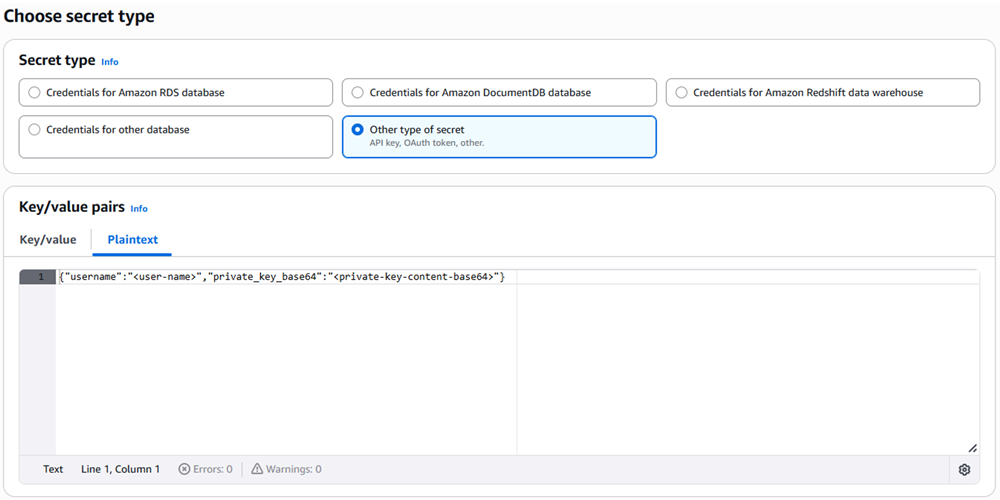
<user-name> is the Snowflake user who is assigned the public key.
<private-key-password> is the key pair encryption passphrase.
<private-key-content-base64> is the base64 encoded key content.
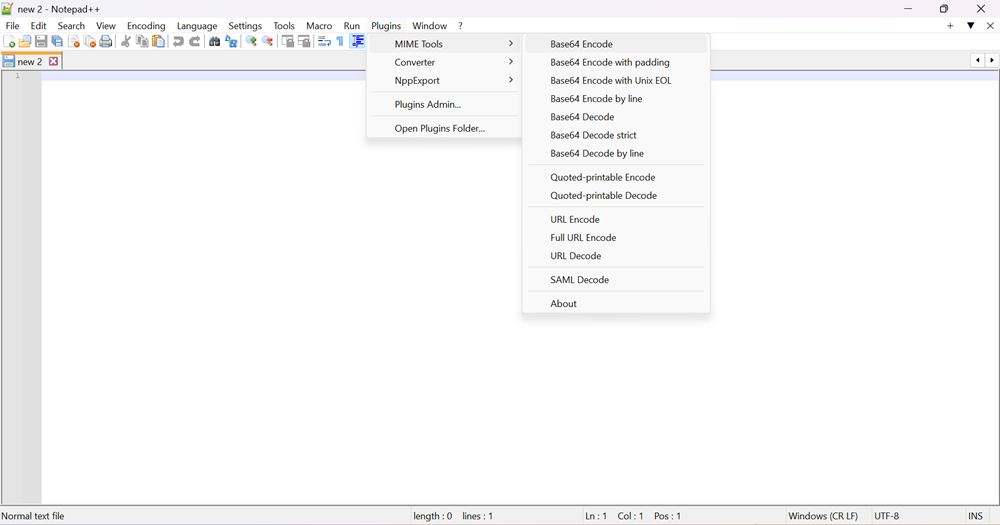
You can copy and select the key content in Notepad++. In Notepad++, click Plugin in the top navigation, click MIME Tools > Base 64 Encode, and paste the generated base64 encoded content in the above field.
Azure Key Vault
Create a secret in Azure Key Vault. For more information, see Set and Retrieve a Secret from Azure Key Vault Using the Azure Portal.
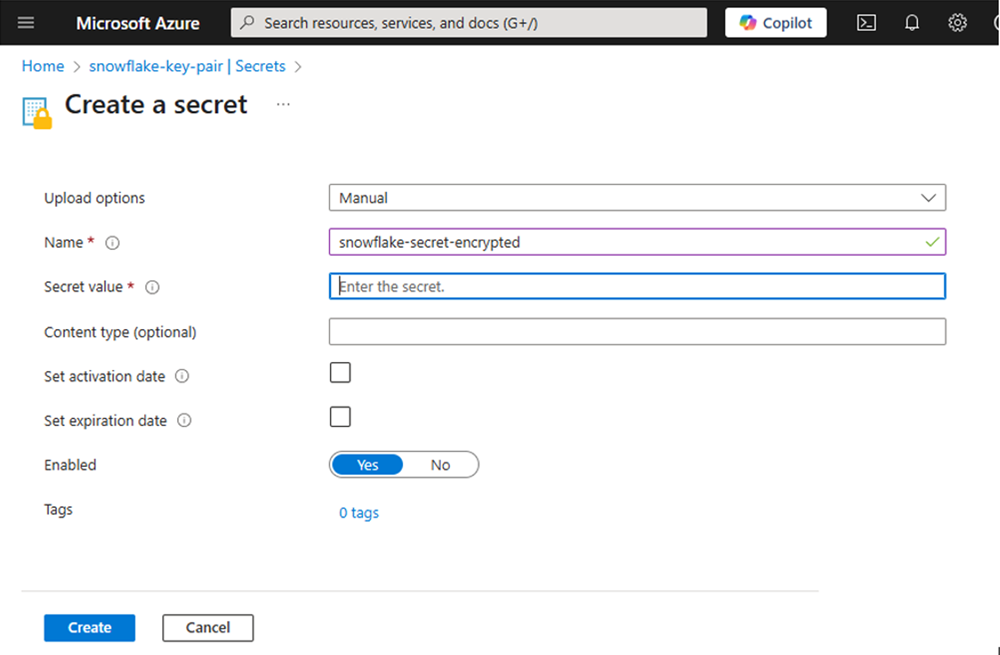
For encrypted keys, use the following format in Secret Value when creating your secret in Azure:
{"username": "<user-name>", "private_key_pwd": "<private-key-password>", "private_key_base64": "<private-key-content-base64>"} For non-encrypted keys, use the following format in Secret Value when creating your secret in Azure:
{"username": "<user-name>", "private_key_base64": "<private-key-content-base64>"}<user-name> is the Snowflake user who is assigned the public key.
<private-key-password> is the key pair encryption passphrase.
<private-key-content-base64> is the base64 encoded key content.
You can copy and select the key content in Notepad++. In Notepad++, click Plugin in the top navigation, click MIME Tools > Base 64 Encode, and paste the generated base64 encoded content in the above field.

Google Secret Manager
Create a secret in Google Secret Manager to store authentication credentials. For more information on creating secrets in Google Secret Manager, see Create a Secret.
Store the key pair authentication as a JSON object. For encrypted keys, use the following JSON format, replacing the values with your details:
{"username": "<user-name>", "private_key_pwd": "<private-key-password>", "private_key_base64": "<private-key-content-base64>"} For non-encrypted keys, use the following JSON format, replacing the values with your details:
{"username": "<user-name>", "private_key_base64": "<private-key-content-base64>"} <user-name> is the Snowflake user who is assigned the public key.
<private-key-password> is the key pair encryption passphrase.
<private-key-content-base64> is the base64 encoded key content.
HashiCorp Vault
Community and Enterprise Editions & HCP Vault Dedicated
Create a secret under a key/value (KV) secret engine in HashiCorp Vault. For more information on creating a secret in HashiCorp Valut, see KV Secrets Engine.
Store the key pair authentication as a JSON object. For encrypted keys, use the following JSON format, replacing the values with your details:
{"username": "<user-name>", "private_key_pwd": "<private-key-password>", "private_key_base64": "<private-key-content-base64>"} For non-encrypted keys, use the following JSON format, replacing the values with your details:
{"username": "<user-name>", "private_key_base64": "<private-key-content-base64>"} <user-name> is the Snowflake user who is assigned the public key.
<private-key-password> is the key pair encryption passphrase.
<private-key-content-base64> is the base64 encoded key content.
HCP Vault Secrets
For HCP Vault Secrets, create a static secret. For more information on creating a static secret in HCP Vault Secrets, see Create Static Secrets.
Store the key pair authentication as a JSON object. For encrypted keys, use the following JSON format, replacing the values with your details:
{"username": "<user-name>", "private_key_pwd": "<private-key-password>", "private_key_base64": "<private-key-content-base64>"} For non-encrypted keys, use the following JSON format, replacing the values with your details:
{"username": "<user-name>", "private_key_base64": "<private-key-content-base64>"} <user-name> is the Snowflake user who is assigned the public key.
<private-key-password> is the key pair encryption passphrase.
<private-key-content-base64> is the base64 encoded key content.
Create a Vault Connection
After you create your secrets above, create a vault connection in Workstation to fetch the secrets. For more information, see Create, Edit, and Delete Vault Connections.
