Strategy One
Configure Web Browser for Integrated Authentication
Integrated Authentication with Kerberos requires that the browser being used to access Strategy
Kerberos should already be configured on the Strategy Library server
Google Chrome on Windows
Chrome reads a key, AuthNegotiateDelegateAllowlist, which configures Chrome to allow certain sites to allow delegation and use Kerberos. The key can be implemented as a policy in a group policy object or added manually in the registry on the client machine where Chrome is installed. To learn more about the policy, see the Google Documentation.
To add the key manually to the registry:
- Close any open instances of Chrome
- Create a key with the path:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Google\Chrome - Add a new 'String value' named
AuthNegotiateDelegateAllowlist. - Populate the value of AuthNegotiateDelegateAllowlist with the host of the Strategy Web site as shown below.
- Add a new 'String value' named AuthServerAllowlist.
-
Populate the value of AuthServerAllowlist with the host of the Strategy Web site as shown below.
If you are using Chrome 85 or earlier, you should use
AuthServerWhitelistandAuthNegotiateDelegateWhitelistinstead ofAuthServerAllowlistandAuthNegotiateDelegateAllowlist.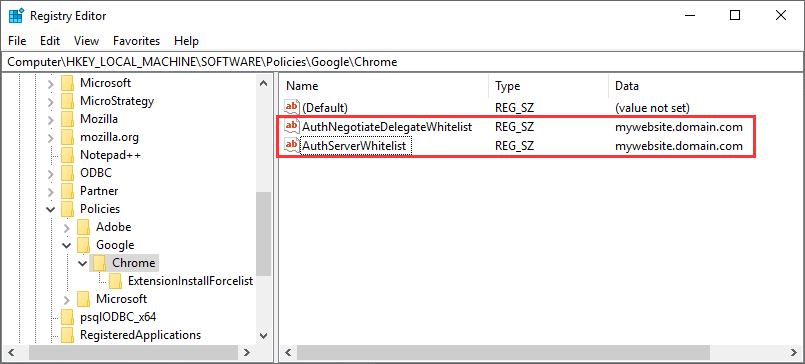
Microsoft Edge on Windows
First, you must configure the browser to recognize Negotiate challenges from Web servers configured to use these types of challenges (as they would be if they were protected by Kerberos).
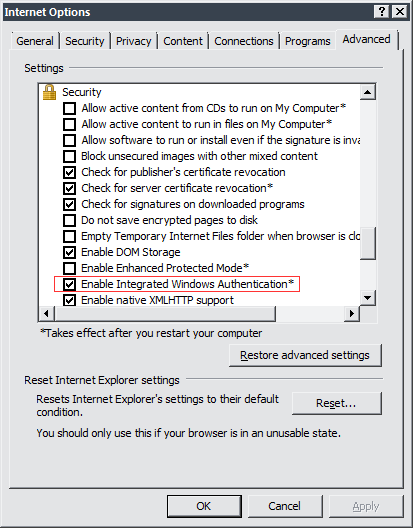
- Open the Windows Control Panel and go to Network and Internet > Internet Options.
- On the Advanced tab, select Enable Integrated Windows Authentication.
See Troubleshoot Kerberos failures on the Microsoft site for more information.
Second, you must also configure the browser to place the Strategy Web site in a security zone that can serve credentials. For security reasons, Edge only allows Kerberos delegation to sites within the Intranet and Trusted Sites zones. For this reason, if Strategy Web is not automatically detected as belonging to either of these zones, you need to add it to one of these zones manually.
-
On the Security tab, click Trusted Sites > Sites.
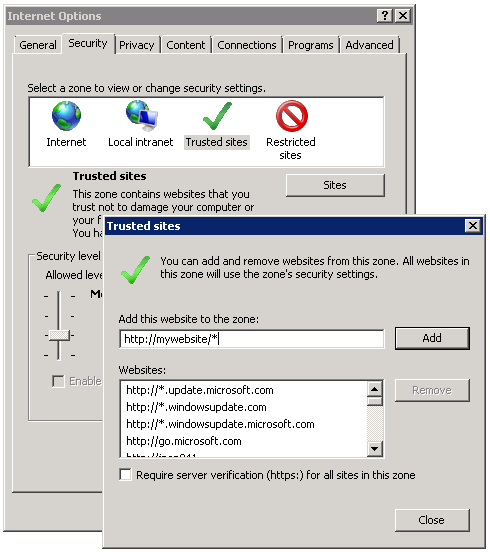
- Enter the hostname for Strategy Web and click Add.
- Click Close.
Third, within the specified zone, double-check the security settings.
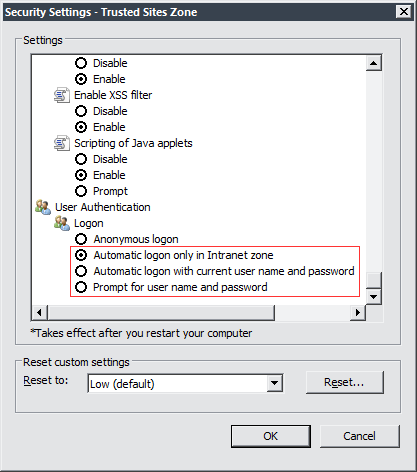
- On the Security tab, click Trusted Sites > Custom Level.
- Under User Authenticaiton > Logon, confirm that Anonymous logon is not selected. Instead, use a setting that allows the browser to pick up user credentials, as shown below.
Add Your Account in macOS
macOS has built in support for Kerberos. You must add your account for Kerberos authentication using either the Ticket Viewer app or kinit command-line tool.
To add your account in the terminal:
-
Enter the following command:
Copy$ kinit user_name@REALM_NAMEuser_name@REALM_NAMEis your user name and realm name. The realm name is case sensitive. -
Enter your password.
Copyuser_name@REALM_NAME's Password:
$
Google Chrome on macOS
-
Once you Add Your Account in macOS, you must configure Chrome’s
AuthServerAllowlistwith any domains that require Kerberos authentication.Run the following command in the terminal:
Copy$ defaults write com.google.Chrome AuthServerAllowlist mywebsite.domain.commywebsite.domain.comis the domain name you need to access with Kerberos authentication. -
You may also need to set
AuthNegotiateDelegateAllowlistto ensure Chrome delegates user credentials on Kerberos authentication.Copy$ defaults write com.google.Chrome AuthNegotiateDelegateAllowlist mywebsite.domain.comIf you are using Chrome 85 or earlier, you should use
AuthServerWhitelistandAuthNegotiateDelegateWhitelistinstead ofAuthServerAllowlistandAuthNegotiateDelegateAllowlist. - You may need to restart your machine for the changes to take effect.
To learn more about the policies, see Chrome Enterprise policy list.
Microsoft Edge on macOS
-
For Edge 77 and later, you must configure Edge’s
AuthServerAllowlistwith any domains that require Kerberos authentication.To learn more about the policy, see AuthServerAllowlist on the Microsoft site.
Run the following command in the terminal:
Copy$ defaults write com.microsoft.Edge AuthServerAllowlist mywebsite.domain.commywebsite.domain.comis the domain name you need to access with Kerberos authentication. -
You may also need to set
AuthNegotiateDelegateAllowlistto ensure Chrome delegates user credentials on Kerberos authentication.Copy$ defaults write com.microsoft.Edge AuthNegotiateDelegateAllowlist mywebsite.domain.com - You may need to restart your machine for the changes to take effect.
Mozilla Firefox
Firefox has two flags, network.negotiate-auth.trusted-uris and network.negotiate-auth.delegation-uris, which configure it to trust certain sites to allow delegation and use Kerberos.
- Navigate to
about:configin the browser. - Find the two flags in the list of configuration settings.
- Double-click on each flag and enter the host of the Strategy Web site, as shown below:

