Version 2021
Security
No PostgreSQL specific customizations were made for this feature.
Securing BI applications and the sensitive data they contain requires resolving the following critical areas of an enterprise software security problem:
- User authentication
-
User authorization, including the following key sub-components:
- Application functionality security
- Access control lists
- Data security
- Internet architecture and transmission security
User Authentication
User authentication is the process of confirming a user’s identity. Validation of user credentials during initial access can be performed:
- Within MicroStrategy using standard authentication
- Outside MicroStrategy using linked authentication with third-party security systems
- Through MicroStrategy Web integration with single sign-on solutions
User Authorization
Within any enterprise application, it is crucial to distinguish between users based on the knowledge, business needs, and security level of each user. Authorization refers to the three-dimensional process by which an application determines.
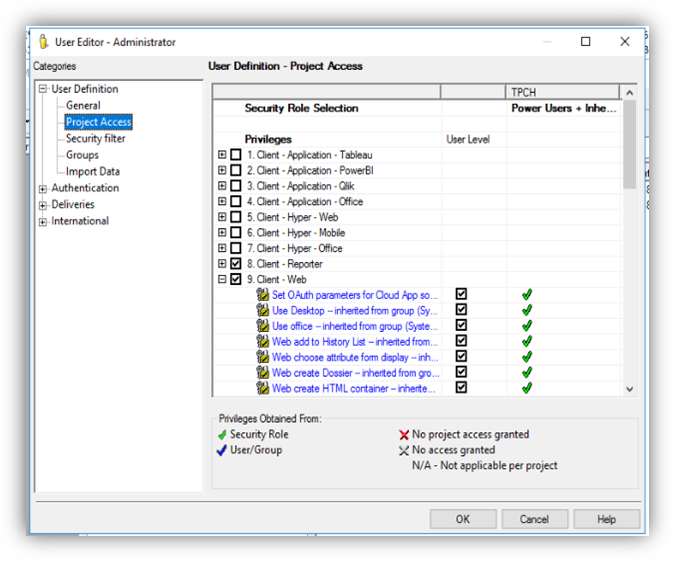
Application Functionality Privileges
MicroStrategy employs over 160 privileges to assign application functionality to users, user roles, and user groups through a graphical interface, and through text-based commands that can be run in batches with Command Manager.
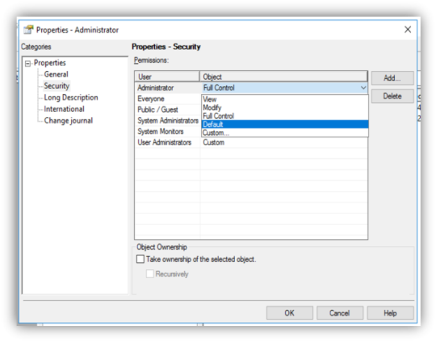
Object Access Permissions
Individual MicroStrategy metadata objects are governed by their own security permissions, called access control lists (ACL). Each data abstraction object, business abstraction object, report component, and report definition may have its own unique ACL, which grants users or user groups a set of privileges for the object.
Data Access Security
In a database, security restrictions for database logins can be placed on tables, rows, and columns. MicroStrategy’s BI platform accesses data sources using database connections. Separate database connections can be created to access the same data source with different logins. MicroStrategy users and user groups are linked to database connections using connection maps. See User Defined Roles for more details about securing data with database security.
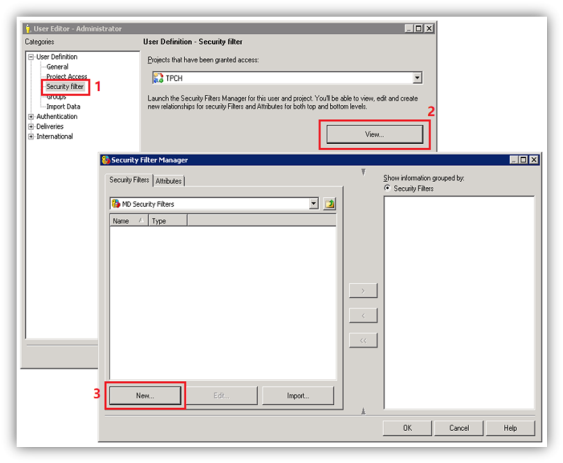
Security filters also provide a method for ensuring row-level data security. All the filtering sophistication available in MicroStrategy can be used to limit the data that a user or user group can access.