Version 2021
User Defined Roles
Administrators can customize a server role with explicit permissions required on databases, credentials, connections, or other permissions. This provides more flexibility for database access control.
This greater flexibility allows administrators to match MicroStrategy personas more specifically with PostgreSQL DB roles. For example, a MicroStrategy Analytics Architect user would expect to have read and write access to the PostgreSQL database, as well as system tables, since the Architect user must have read and edit access to the warehouse catalog. A Reporter user on the other hand only needs read access to database. Connection mapping can map those MicroStrategy users to different database users with different roles. Here is an example of how connection mapping can be implemented:
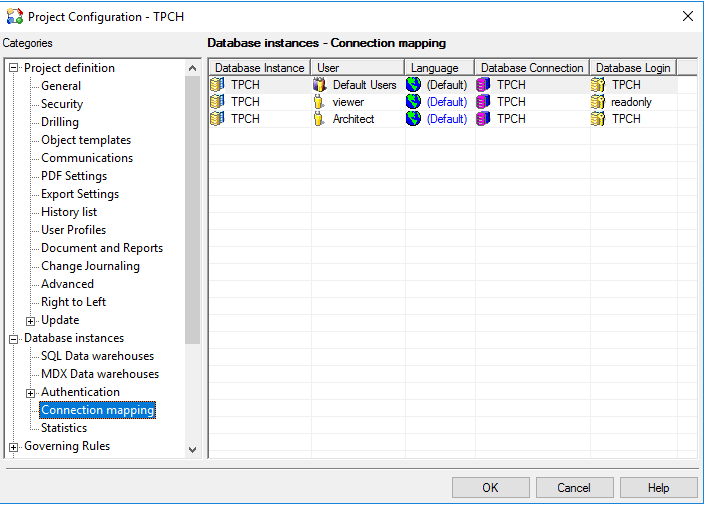
When performing operations that can eventually write data back to database, the following execution failure error may be returned:
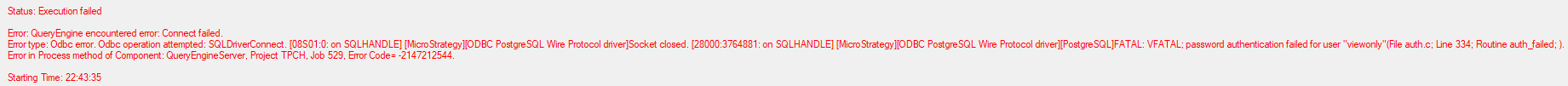
In PostgreSQL, users with read access to the database have read access to system tables by default. Users who have read access to system tables can access the catalog. This means by default, users can execute the warehouse catalog. With the MicroStrategy security model, very few users are given access to the warehouse catalog to ensure the security of the database.
