Strategy ONE
Authentication Modes Supported by MicroStrategy Web
A user is considered to be authenticated in a MicroStrategy Web environment when a supported authentication authority verifies that the identification information, or credentials, provided by or supplied for the user are valid. MicroStrategy Web supports a number of authentication modes for performing this verification. The MicroStrategy Web administrator determines which authentication modes are available to users, but the choice of an authentication mode generally depends on how user data is stored within a company's environment. Companies traditionally store user data in a database, a Windows domain, or a directory server.
By default, MicroStrategy Web supports the following authentication modes for verifying the user's credentials. Each login mode specifies a particular mechanism or authority to be used for authentication.
-
Windows NT authentication: The Windows NT SID (security identifier) is validated against the NT logon context stored in the MicroStrategy metadata repository. The Windows domain is the authentication authority.
If you use Windows NT/2000 or later as your network operating system and your users are already defined in the Windows domain, they can access MicroStrategy Web without having to enter a login ID and password, providing out-of-the-box single sign-on.
-
Integrated authentication: The Kerberos token is validated using the Kerberos authentication protocol. The Kerberos KDC (Key Distribution Center) is the authentication authority.
-
Trusted authentication: The credentials entered by or supplied for the user are validated against the credentials stored in a trusted authentication provider, such as CA SiteMinder, IBM Tivoli Access Manager, or Oracle Identity Manager (referred to as Oblix). The trusted authentication provider is the authentication authority.
-
Standard authentication: The credentials entered by or supplied for the user are validated against the credentials stored in the MicroStrategy metadata repository. MicroStrategy Intelligence Server is the authentication authority.
-
LDAP authentication: The credentials entered by or supplied for the user are validated against the credentials stored in an LDAP (Lightweight Directory Access Protocol) directory. The LDAP directory is the authentication authority.
-
Database authentication: The credentials entered by or supplied for the user are validated against the credentials stored in a data warehouse database. The RDBMS (Relational Database Management System) is the authentication authority.
-
Guest authentication: Anonymous, or guest, authentication requires no credentials so there is no authentication authority. Access to MicroStrategy content and functionality is generally limited with this authentication mode.
In addition to providing default support for the authentication authorities listed above, MicroStrategy Web allows you to use a custom External Security Module to perform custom authentication.
The diagram below illustrates how the various authentication modes operate within a MicroStrategy environment:
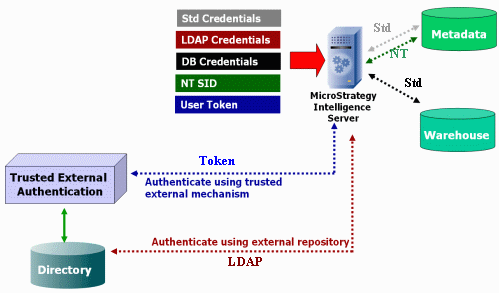
As shown in the diagram above, the information needed for authentication (that is, the login credentials and other user profile information for a MicroStrategy user) can be stored in the MicroStrategy metadata or in an external repository, such as an LDAP directory or a database designed to serve as a user repository. This flexibility allows you to use an external authentication mechanism to authenticate a user (that is, to verify that the user is who they say they are) and then use MicroStrategy to authorize (that is, to permit access to a specific resource) this authenticated user. It also prevents you from having to create a separate set of users for the MicroStrategy application if they already exist somewhere else. You can also use your external user repository to store information about whether each user in that repository has access to the MicroStrategy application.
For an explanation of each authentication mode and instructions on how to set up MicroStrategy authentication, see the "MicroStrategy System Administration Guide".
