Version 2021
SSL Encryption
SSL must be enabled to use an SSL encrypted connection for PostgreSQL. Then, you can apply SSL encryption for DSN and DSN-less connections in MicroStrategy products. Starting in MicroStrategy 2021 Update 3, SSL encryption is enabled when creating DSN-less connections by default. See KB485177: How to connect to Microsoft Azure PostgreSQL for more details.
PostgreSQL has native support for using SSL connections to encrypt client/server communications for increased security. This requires the installation of OpenSSL on both client and server systems and that support in PostgreSQL is enabled at build time. See Secure TCP/IP Connections with SSL on the PostgreSQL site for more details.
Azure Database for PostgreSQL, by default, is configured to require a TLS/SSL connection. See Configure TLS connectivity in Azure Database for PostgreSQL - Single Server on the Microsoft site for more information about TLS/SSL configuration for Azure Database for PostgreSQL.
Create SSL Enabled DSN on Windows
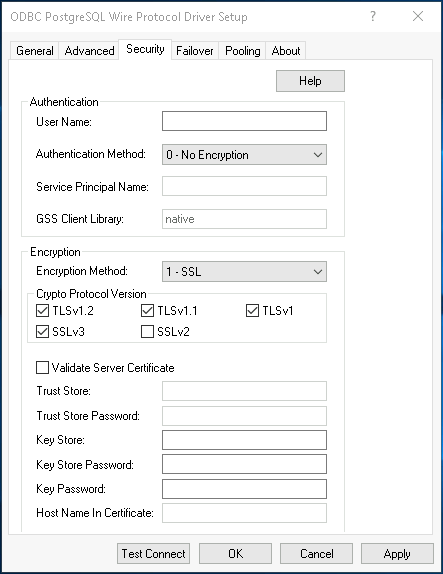
Set up one of the following protocols.
-
Set the Encryption Method to SSL.
-
In Crypto Protocol Version, select your SSL version.
-
Select Validate Server Certificate if it’s required in your scenario and specify the certificate path in Trust Store.
Set the SSL Mode based on your scenario. For example, you can set the SSL Mode to require.
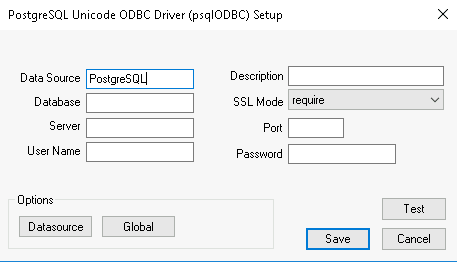
Create SSL Enabled DSN on a Linux Platform
Set up one of the following protocols.
DSN-less Connection String with SSL Enabled
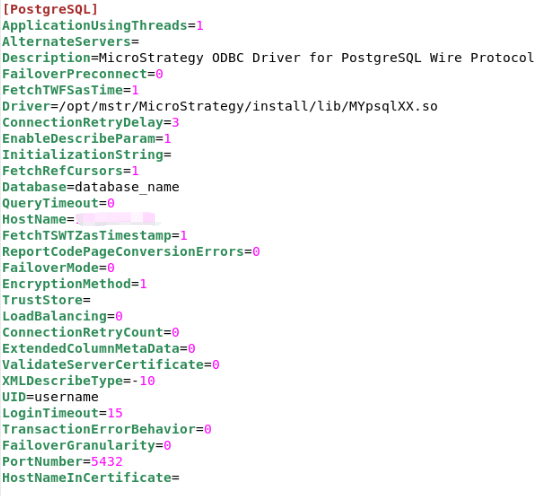
DRIVER={MicroStrategy ODBC Driver for PostgreSQL Wire Protocol}; HostName={hostname}; PortNumber={port}; Database={database};EncryptionMethod=1; ValidateServerCertificate=0;
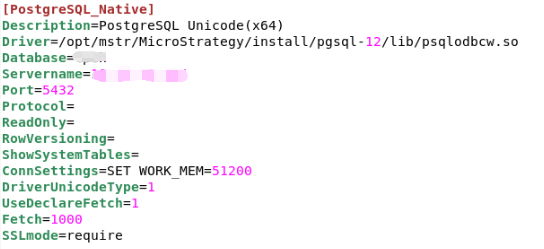
DRIVER={PostgreSQL Unicode(x64)}; Servername={hostname}; Port={port}; Database={database}; DriverUnicodeType=1;UseDeclareFetch=1;Fetch=1000;SSLmode=require;
JDBC;DRIVER={com.microstrategy.jdbc.postgresql.PostgreSQLDriver};URL={jdbc:microstrategy:postgresql://{hostname}:{port};DATABASENAME={database};EncryptionMethod=SSL;ValidateServerCertificate=false;fetchTWFSasTime=TRUE};