MicroStrategy ONE
Enabling Single Sign-On with SAML Authentication for ASP Web and Mobile
You can configure MicroStrategy ASP Web and Mobile to support SAML using Shibboleth Service Provider for IIS.
Shibboleth Service Provider Setup
Shibboleth Service Provider Configuration
Identity Provider Configuration
In MicroStrategy 9.0 and above, ACL-based protection is supported for Admin pages (asp/Admin.aspx and asp/TaskAdmin.aspx). By default, only administrators have access to Admin pages.
Additionally, in MicroStrategy 11.0 a new feature to protect Admin pages was introduced using Windows IIS URL Authorization. By default, the URL Authorization feature is not installed by the Windows OS. IIS URL Authorization is supported by IIS 7.0 and above. You can find instructions to install IIS URL Authorization here.
The authorization rule has been added to Web.config out of the box. Once you install the IIS URL Authorization module, you will automatically get protection for Admin pages.
Compared to the ACL based protection, IIS URL authorization has a centralized configuration in Web.config.
Shibboleth Service Provider Setup
- Install the latest version of Shibboleth Service Provider.
- Follow the installation instructions from Shibboleth for your version of IIS.
Configuring the New Plugin
This is best done from the command line. You will also need admin privileges.
Configuring the IIS7 DLL
From the C:\Windows\System32\InetSrv directory, run the following lines:
appcmd install module /name:ShibNative32 /image:"c:\opt\shibboleth-sp\lib\shibboleth\iis7_shib.dll" /precondition:bitness32
appcmd install module /name:ShibNative /image:"c:\opt\shibboleth-sp\lib64\shibboleth\iis7_shib.dll" /precondition:bitness64The Shibboleth 3.2.3 Windows installer contains a Configure IIS7 module option to automatically install the Shibboleth module into IIS. If this option is selected, you can skip running appcmd.
Verifying the installation
Open the following URL:
https://localhost/Shibboleth.sso/StatusThis must be run as localhost, and should return XML containing information about Shibboleth. The latest Shibboleth version only supports HTTP connections.
MicroStrategy Integration
Integration with MicroStrategy ASP Web
- Setup the Trust relationship between MicroStrategy Web and Intelligence Server:
- Open the admin page at
https://localhost/MicroStrategy/asp/Admin.aspx - Go to Intelligence Servers > Servers
- For each Intelligence Server, go to Properties > Modify
- Click on "Trust relationship between Web Server and MicroStrategy Intelligence Server".
- Enter credentials. When successfully setup, there should be a check mark next to the trust.
- Open the admin page at
- Navigate to Intelligence Servers > Default properties > Login.
- Enable Trusted Authentication Request log-in mode.
- Under Trusted Authentication Provider select Custom SSO.
- Configure
C:\Program Files (x86)\MicroStrategy\Web ASPx\WEB-INF\classes\resources\custom_security.propertiesparameterLoginParamwith same value associated with the user mapped from the SAML assertion.If the HTTP header in attribute-map.xml is set to id="SBUSER", then custom_security.properties must be LoginParam=SBUSER.
MicroStrategy User Mapping
Ensure Intelligence Server users are mapped to your SAML users as identified by the UID. Access User Manager, either with MicroStrategy Developer or the Intelligence Server Administration Portal in MicroStrategy Web.
MicroStrategy Developer
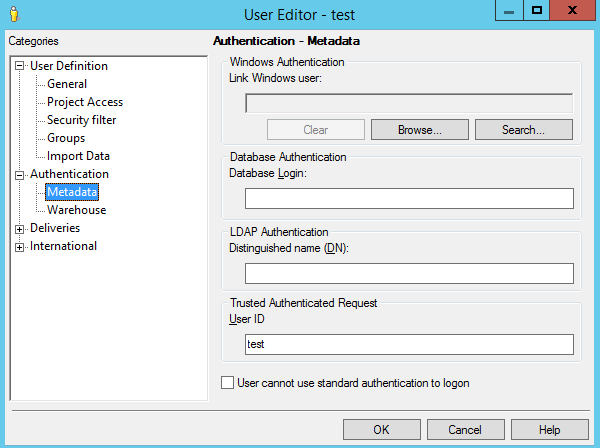
To map users using MicroStrategy Developer, open: User Manager > Edit User Properties > Authentication > Metadata > Trusted Authentication Request > User ID.
Intelligence Server Administration Portal on MicroStrategy Web
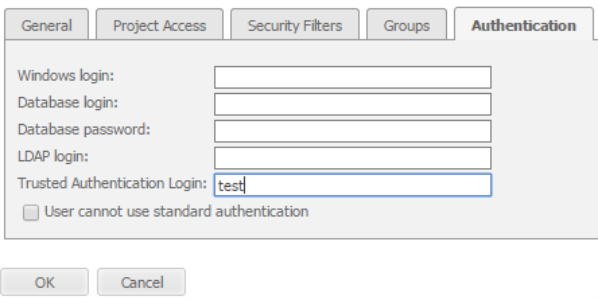
To map users through the Web Administration Portal, go to: MicroStrategy Web > Intelligence Server Administration Portal > User Manager > Edit User Properties > Authentication > Trusted Authentication Login.
Shibboleth Service Provider Configuration
To configure the Shibboleth Service Provider, use the following instructions in conjunction with the Shibboleth documentation.
- Configure
%SHIBBOLETH_INSTALL_DIR%\etc\shibboleth\shibboleth2.xml -
Set useHeaders to true in <ISAPI>
Copy<ISAPI normalizeRequest="true" safeHeaderNames="true" useHeaders="true"> - Replace site name with a fully qualified site name:
shibboleth2.xml – site
Copy<Site id="1" name="sp.example.org"/>with
Copy<Site id="1" name="FULLY_QUALIFIED_SERVICE_PROVIDER_HOST_NAME"/> - Replace host name with fully qualified name, and paths:
shibboleth2.xml – host
Copy<Host name="sp.example.org">
<Path name="secure"
authType="shibboleth"
requireSession="true"/>
</Host>with
Copy<Host name="FULLY_QUALIFIED_SERVICE_PROVIDER_HOST_NAME">
<Path name="MicroStrategy"
authType="shibboleth"
requireSession="true"/>
<Path name="MicroStrategyMobile"
authType="shibboleth"
requireSession="true"/>
</Host> - Replace entityID value with a suitable entity name for your new service provider:
Make note of this value, as it will be required by the Identity Provider.
shibboleth2.xml-entityIDCopy<ApplicationDefaults entityID="https://sp.example.org/shibboleth"
REMOTE_USER="eppn persistent-id targeted-id"
cipherSuites="ECDHE+AESGCM:ECDHE:!aNULL:!eNULL:!LOW:!EXPORT:!RC4:!SHA:!SSLv2">with
Copy<ApplicationDefaults entityID="https://FULLY_QUALIFIED_SERVICE_PROVIDER_HOST_NAME/shibboleth"
REMOTE_USER="eppn persistent-id targeted-id"
cipherSuites="ECDHE+AESGCM:ECDHE:!aNULL:!eNULL:!LOW:!EXPORT:!RC4:!SHA:!SSLv2"> - Set SSO entityID with your SAML Identity Provider: This may be obtained from the Identity Provider metadata by replacing:
shibboleth2.xml - Identity Provider
Copy<SSO entityID="https://idp.example.org/idp/shibboleth"
discoveryProtocol="SAMLDS" discoveryURL="https://ds.example.org/DS/WAYF">
SAML2 SAML1
</SSO>with the following:
Copy<SSO entityID="YOUR_SSO_SAML_ENTITY_ID">
SAML2 SAML1
</SSO>Values for
discoveryProtocolanddiscoveryURLare only required with Shibboleth Identity Provider. - Obtain Identity Provider metadata:
- URL option (recommended): If IdP exposes a metadata endpoint, this is the preferred solution, otherwise see File option below. Add the following declaration below the commented out
<MetadataProvider>section:shibboleth2.xml - Identity Provider metadata
Copy<MetadataProvider
type="XML"
url="https://adfs.example.org/federationmetadata/2007-06/federationmetadata.xml"/> - File option: Copy it to the file
%SHIBBOLETH_INSTALL_DIR%\etc\shibboleth\partner-metadata.xml. Uncomment the following declaration inshibboleth2.xml:shibboleth2.xml - Identity Provider metadata
Copy<MetadataProvider
type="XML"
file="partner-metadata.xml"/>
- URL option (recommended): If IdP exposes a metadata endpoint, this is the preferred solution, otherwise see File option below. Add the following declaration below the commented out
- Configure
%SHIBBOLETH_INSTALL_DIR%\etc\shibboleth\attribute-map.xmlto extract several fields from the SAML assertion, which MicroStrategy will associate with an Intelligence Server user. See AttributeNaming on the Shibboleth site for more information.- Add the <Attribute> mappings under <Attributes> root. Shibboleth will look for this assertion attribute and map it to the HTTP header SBUSER for the MicroStrategy application to consume. Here is a configuration for ADFS where we read the windows account name claim. This must be consistent with the Identity Provider claim mapping that will be configured later.
attribute-map.xml user mapping - ADFS
Copy<Attribute
name="http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname"
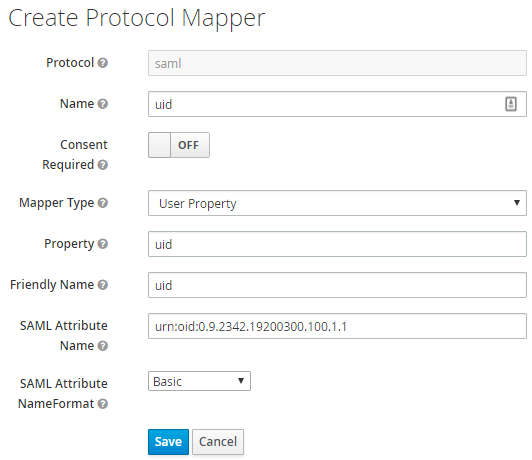
id="SBUSER"/>Here is a sample configuration for Keycloak, where you read the "urn:oid:0.9.2342.19200300.100.1.1" or UID claim :
attribute-map.xml user mapping
Copy<Attribute
name="urn:oid:0.9.2342.19200300.100.1.1"
id="SBUSER"
nameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"/>It is also recommended to comment out the unused <Attribute> declarations in attribute-map.xml.
- Add the <Attribute> mappings under <Attributes> root. Shibboleth will look for this assertion attribute and map it to the HTTP header SBUSER for the MicroStrategy application to consume. Here is a configuration for ADFS where we read the windows account name claim. This must be consistent with the Identity Provider claim mapping that will be configured later.
- Restart the following services:
- Verify XML is returned from
https://localhost/Shibboleth.sso/Statusagain. Also, ensure the Application entityID and MetadataProvider source values have been correctly configured in previous steps.
Identity Provider Configuration
It is necessary to (1) add the Service Provider configured above as a new client in the SAML Identity Provider (for example, ADFS), and (2) ensure that the user login/UID is also included in the SAML Assertion. Some guidance is provided below for several Identity Providers - refer to their documentation for adding new clients/relying parties for details.
ADFS
- Run the Microsoft Windows Server Manager.
- Under Tools run ADFS Management.
- Expand to the following: ADFS > Trust Relationships > Relying Party Trusts.
- Click Add Relying Party Trust to launch the wizard.
- When you reach the "Select Data Source" option, you need the Shibboleth Service Provider metadata. Enter:Copy
https://YOUR_MICROSTRATEGY_WEB_URL/Shibboleth.sso/Metadata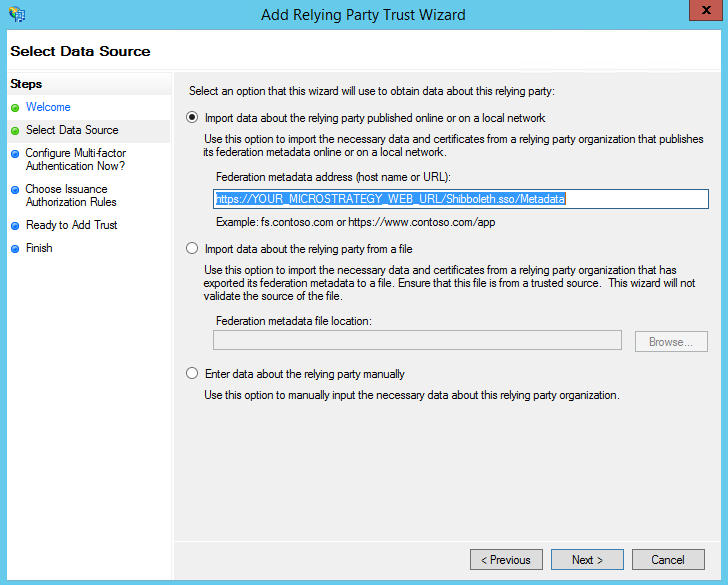
If the HTTP URL metadata does not work, you may have to manually download and upload the metadata file.
- For "Display name", it is recommended you use YOUR_MICROSTRATEGY_WEB_URL.
- When finished, you may be prompted to edit claim rules. If not, you can right-click your new client and select Edit claim rules.
- Click Add Rule under the tab Issuance Claim Rules.The Add Transform Rule Claim Wizard appears.
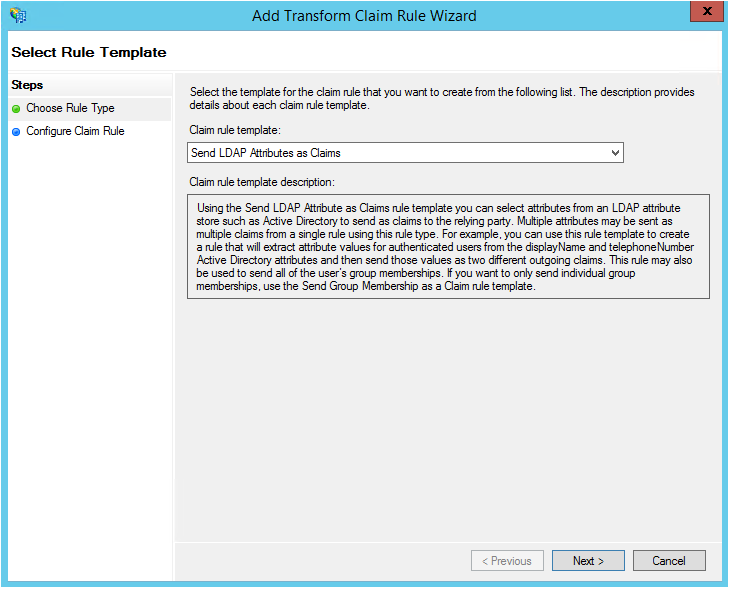
- If your ADFS is backed by LDAP, select Send LDAP Attributes as Claims. Otherwise, refer to ADFS documentation.
- Set the following fields to values consistent with the Shibboleth
attribute-map.xmlconfiguration from above.- Claim rule name: user
- Attribute store: Active Directory
- Mapping: LDAP Attribute=SAM-Account-Name, Outgoing Claim Type=Windows account name
Keycloak
The Identity Provider will need ensure the user identity field is also included in the SAML assertion generated when a user is authenticated. The exact field depends upon the Identity Provider. The user identity will be associated with the SAML parameter name of urn:oid:0.9.2342.19200300.100.1.1. This parameter must be consistent with the parameter with the same name in the Shibboleth Service Provider attribute-map.xml declaration.